Note: AVI Networks is also referenced as NSX Advanced Load Balancer as the product is absorbed into the VMware Solutions
The AVI Vantage controller has the ability to generate self-signed certificates for use with your services. As Self-Signed will not be trusted by your browser, it is recommended that you only use these for testing your environments.
Generating a Self-Signed certificate with an exportable private key in the UI is quite simple.
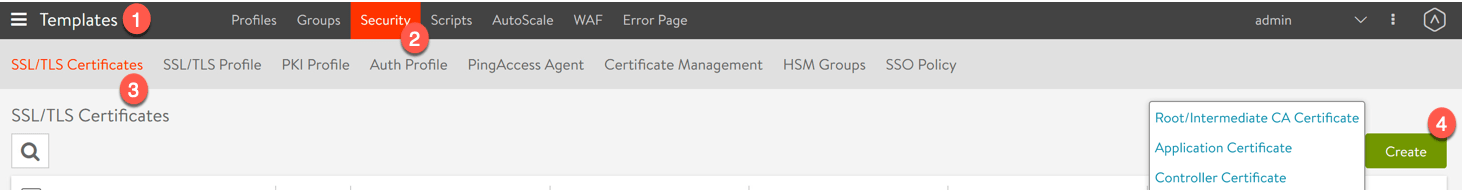
1. Go to the Templates view
2. Select the Security tab
3. Select the SSL/TLS Certificates tab
4. Click the green Create button, and select your type of certificate. (in my example I am creating an application certificate)
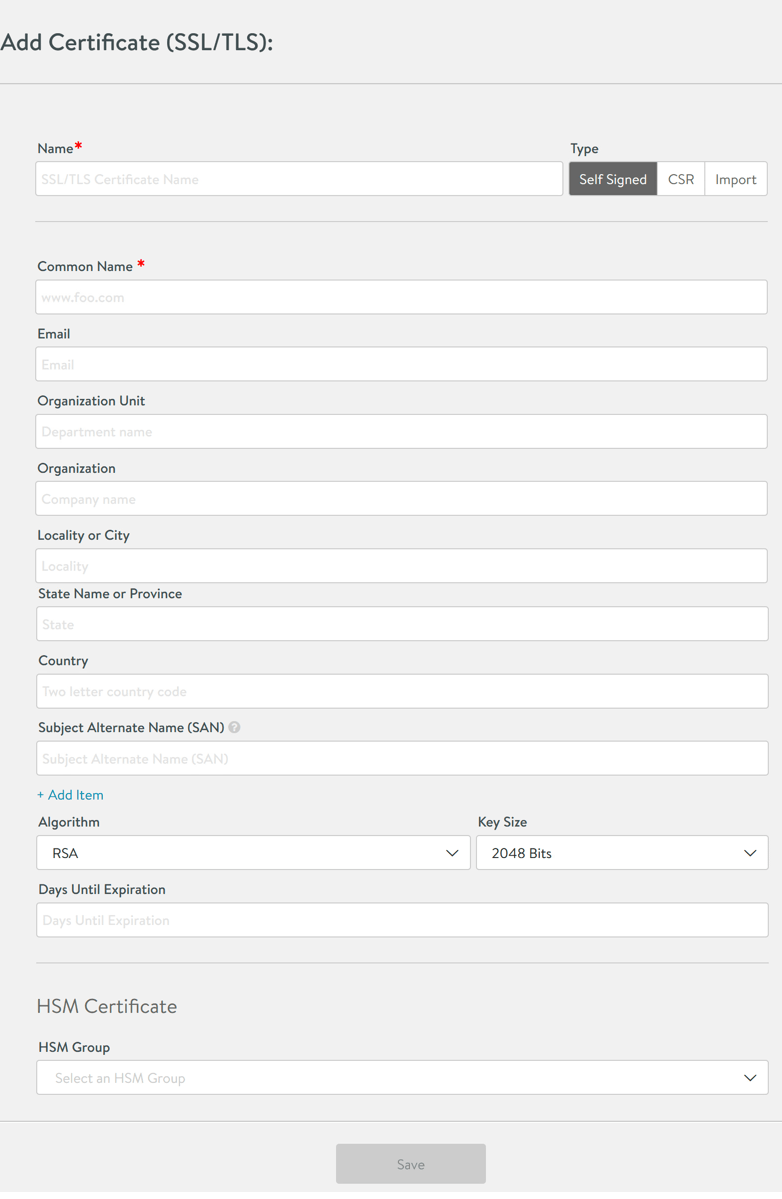
Filling out the forms, the options are as you would expect when working with generating a CSR and CAs.
Fill in your details and click Save.
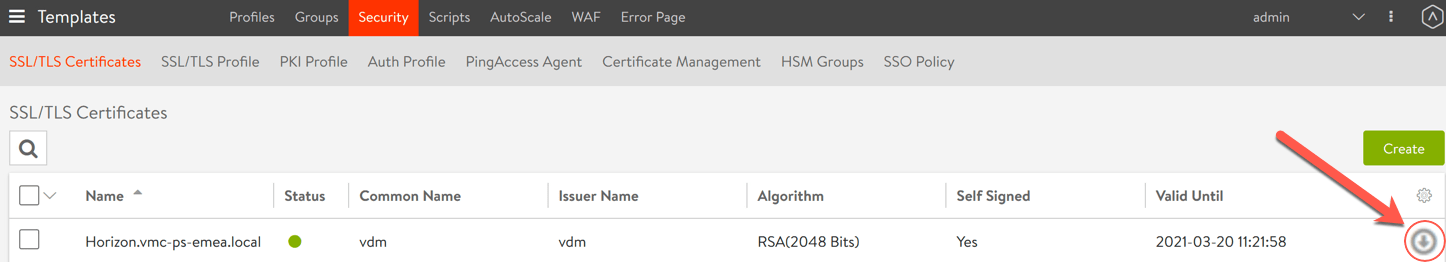
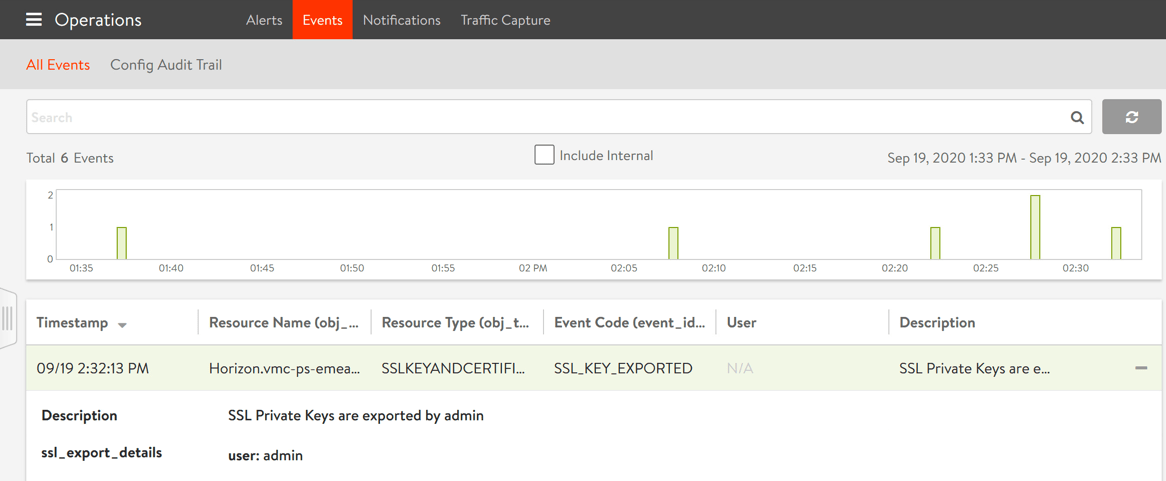
Once you have a SSL generated, the next step is downloading for use with your servers.
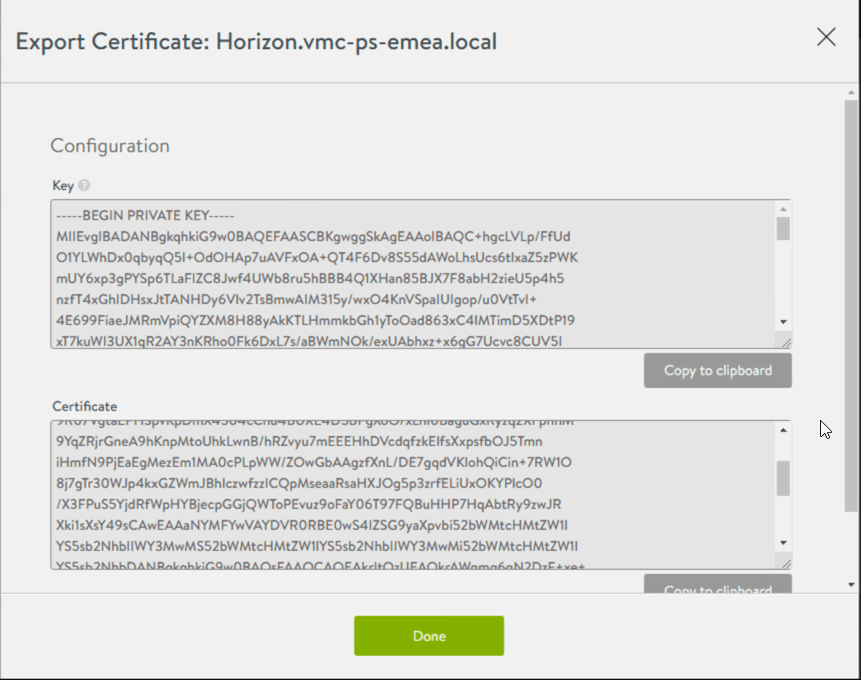
As you can see, clicking download doesn’t give you a usable SSL file with the private key, so you need to use a tool such as OpenSSL to take the output and convert it into a usable format. Continue reading for the steps.
Note: Viewing or exporting the private key generates a system event, tracking the administrator’s export action. Avi Networks recommends using role-based access to control which users are allowed to use a certificate versus export the key.
You can see this below.
Using OpenSSL to convert the CSR into a PFX file
Download OpenSSL if you do not already have it.
Save the above SSL outputs from AVI Networks interface to two files;
- Key > certficate.key
- Certificate > certificate.crt
Next we will run the following command which will create a single PFX file that contains the exportable key.
openssl pkcs12 -export -out {file_name.pfx} -inkey {private key file} -in {CRT file}
After entering the command, you will be prompted to enter and verify an export password to protect the PFX file. You will use this to export the certificates and key.
Breakdown of the command;
openssl – the command for executing OpenSSL pkcs12 – the file utility for PKCS#12 files in OpenSSL -export -out certificate.pfx – export and save the PFX file as certificate.pfx -inkey privateKey.key – use the private key file privateKey.key as the private key to combine with the certificate. -in certificate.crt – use certificate.crt as the certificate the private key will be combined with. (Source)
For me, I needed this for us with VMware Horizon, if you hadn’t already realised from the earlier screenshots. So to complete my use case, its a case of opening up the MMC and Certificates snap-in, import the PFX file and input the password.
Regards