In this blog post, I am going to take you through how to get started with VMware Aria Hub, and connect your first public cloud account, in this example, AWS.
What is VMware Aria Hub?
Before we dive into the technical pieces, what is VMware Aria Hub?
If we take the marketing definition:
VMware Aria Hub is a transformational multi-cloud management solution unifying cost, performance, and config and delivery automation in a single platform with a common control plane and data model for any cloud, any platform, any tool, and every persona
To make this simple, VMware Aria Hub is one of the key SaaS based services which sits at the center of the new VMware Aria Cloud Management platform. In which it gives you a single control plane to be able to access and interrogate data across the previously named vRealize Suite of products, now rebranded as Aria [insert product name], store metadata from all of your Infrastructure platforms (VMware, AWS, Azure, Google) and in the future, bring in data from third party systems.
This centralization of data is key. That part in VMware Aria, is called “Aria Graph”, which uses an Entity Datastore, a component derived from an existing VMware product, CloudHealth SecureState product (now VMware Aria Automation for Secure Clouds). This unique component, which is based on GraphQL, provides the product a unique way to store data, query into other products, and enable the consumer to write new data into the platform as well.
Let’s take this practical example, I have my application which is made up of the typical three tier app standards:
- Load Balancer – AWS
- 2 x Web Servers – AWS
- App Server – AWS
- Database Server – On-Prem DC – vSphere
All these components are deployed by Aria Automation (vRealize Automation), monitored by Aria Operations (vRealize Operations), with application logs sent to Aria Operations for Logs (vRealize Log Insight). The AWS environment is further secured by Aria Automation for Secure Clouds (CloudHealth SecureState), which ensures a number of specific resource tags exist, and they conform to the appropriate CIS benchmark.
Now If I need to query the following information for my application; App owner (who deployed it), Cost Centre, Resource Sizing, and active security alerts. I will need to pretty much either browse the UI or query the API for each of the products mentioned.
By leveraging the new capabilities of VMware Aria Hub, I can browse a single interface to reference all the components of my application, and where this data is stored into the other Aria products, it will pull that data through for me. This would be the same if I am querying for information via the VMware Aria Graph as well, for my programmatic access.
Watch the recording!
As a growing trend is video content, I’ve also produced a recording of the same content of this blog post! So, you can follow along below!
Getting Started with Aria Hub
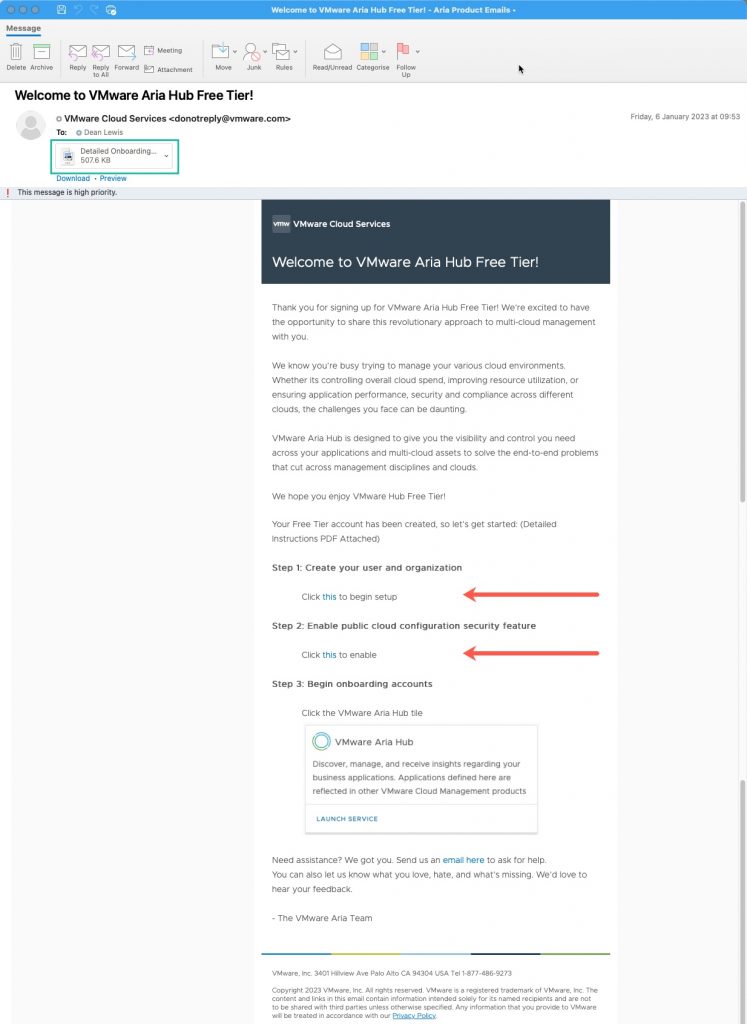
First, you should have an email from VMware welcoming you to the VMware Aria Hub Free Tier. Below I’ve provided a sample email, there are three things to note;
- You need to click on the links in step 1 + 2 to activate the VMware Aria Hub product within the VMware Cloud Services Portal, and enable the Free Tier for VMware Aria Automation for Secure Clouds, which provides the Public Cloud Security Features into the Aria Hub UI
- To setup your VMware Cloud Services Portal organisation and enable the product, there is a PDF attached to the email showing the step-by-step instructions and screenshots if needed (shown in the green box).
Once enabled, in the VMware Cloud Services Portal, click the VMware Aria Hub tile (as in the above email screenshot, step 3).
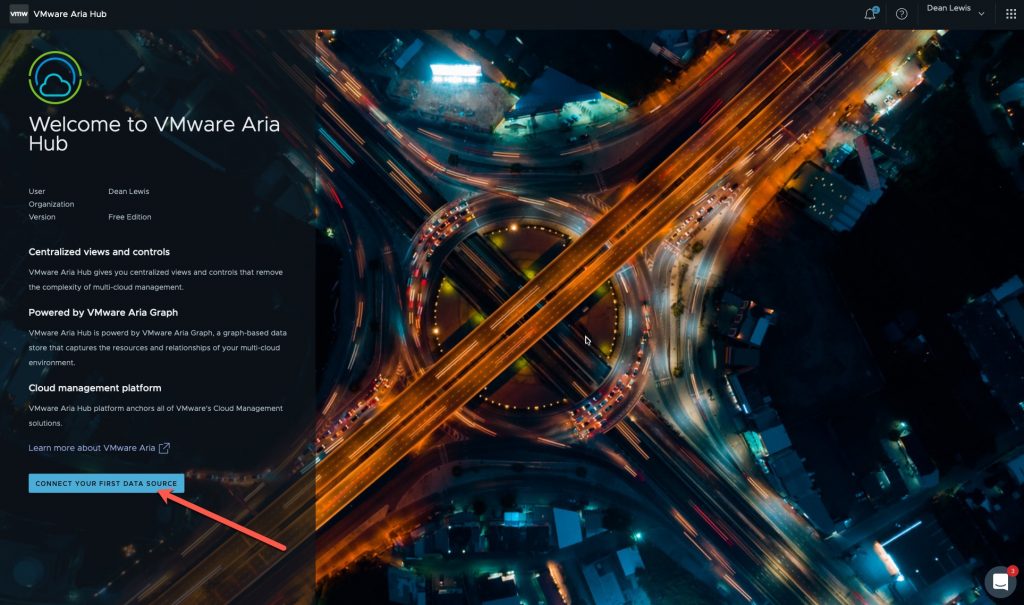
This will present you with the below opening page.
To get started, you only have one option here:
- Click the “Connect your first data source” blue button.
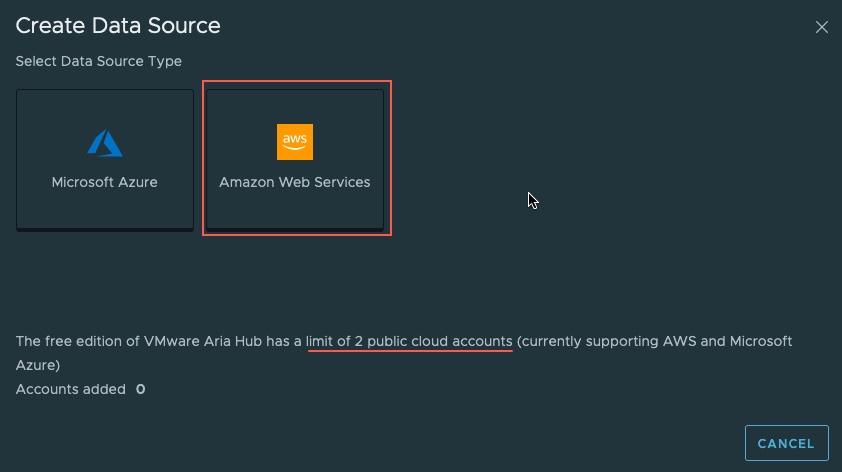
Select which data source type you want to configure. In this blog post we’ll cover AWS setup.
As highlighted, in the Free Tier, you are limited to configuring only 2 public cloud accounts in total. They can be one of each AWS and Azure, or both of same option (i.e. 2 x AWS or 2 x Azure).
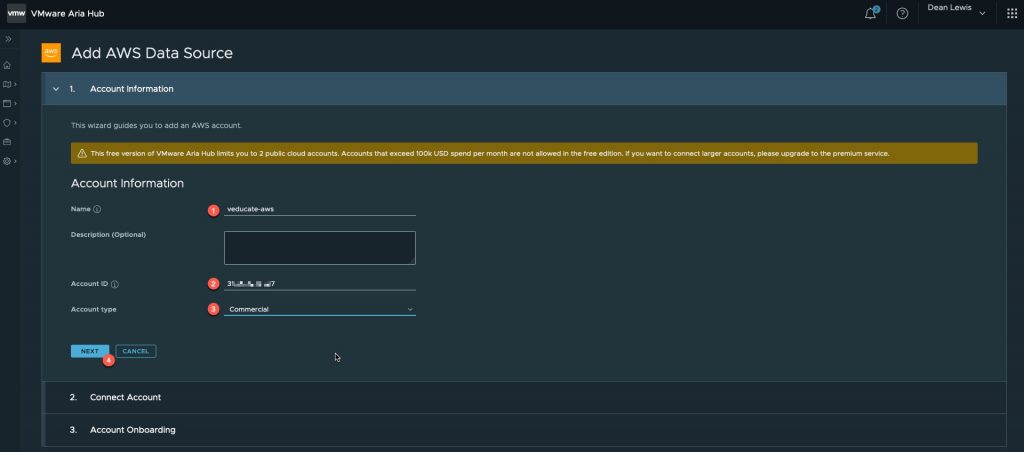
- Provide a friendly name for the Account you are configuring
- Provide your AWS Account ID
- The account type cannot be changed from “Commercial”
Click Next.
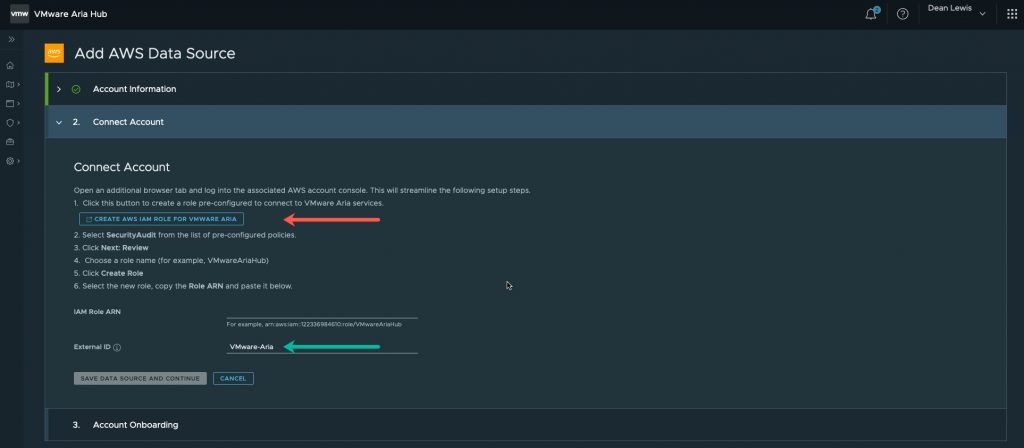
Now we need to create a pre-configured role in AWS, which allows VMware Aria Hub to connect to the public cloud service and pull data. This is quite simple to do, as you are given an easy click button which takes you through the process in the AWS Console.
- Ensure you are already logged into the AWS Console
- Click the blue button “Create an AWS Role for VMware Aria”
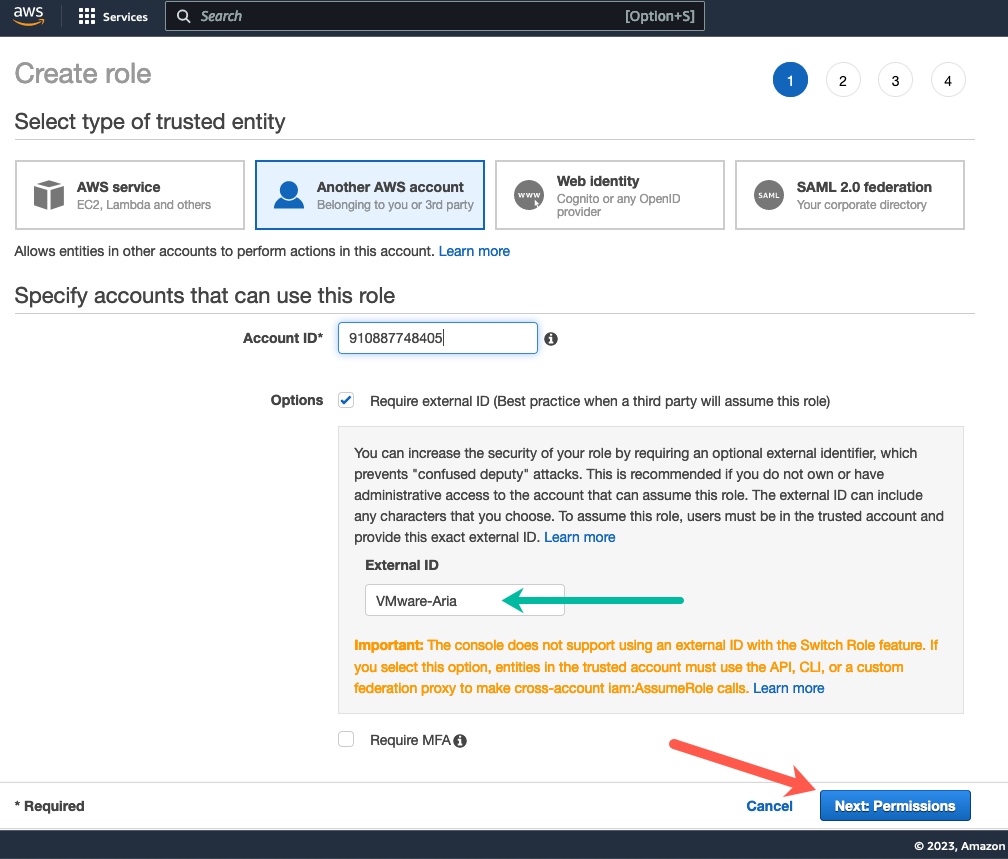
Clicking the above link will take you to the AWS console to create a role, most of the necessary fields will be filled out for you.
- You can change the account ID and external ID if you wish, but you will need to note any changes for the later steps. I left mine as provided.
- Click “Next: Permissions”
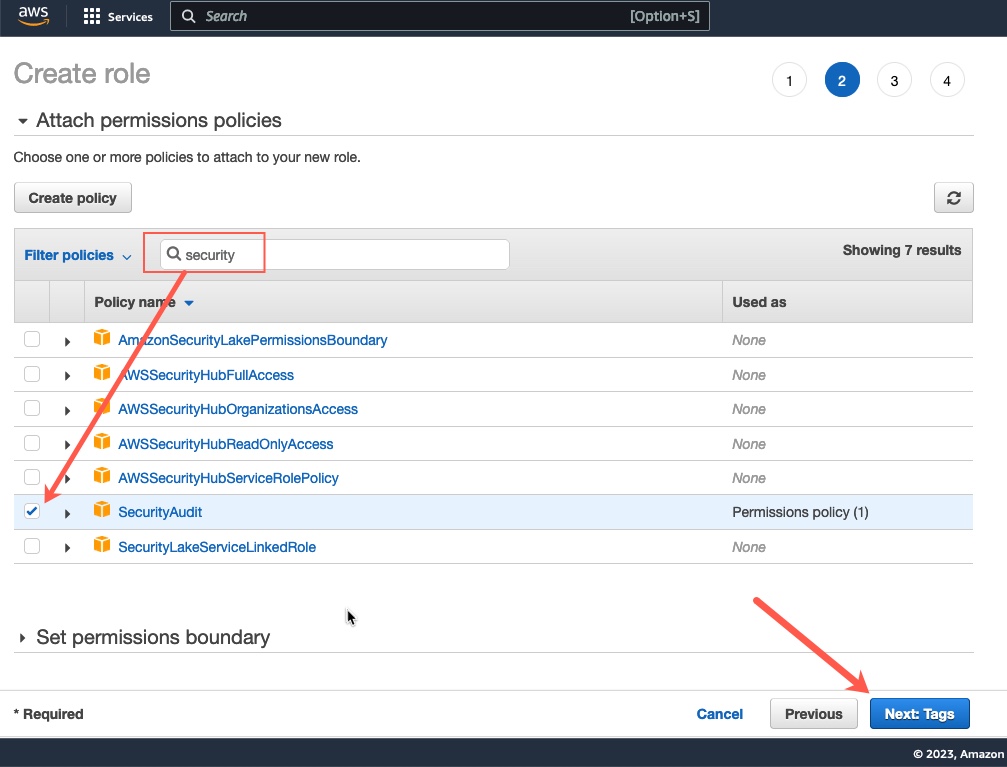
- Search for the permissions policy named “SecurityAudit” ensure that it is selected with a tick.
- Click “Next: Tags”
I skipped the tags screens and didn’t add any. Next to the Review Screen.
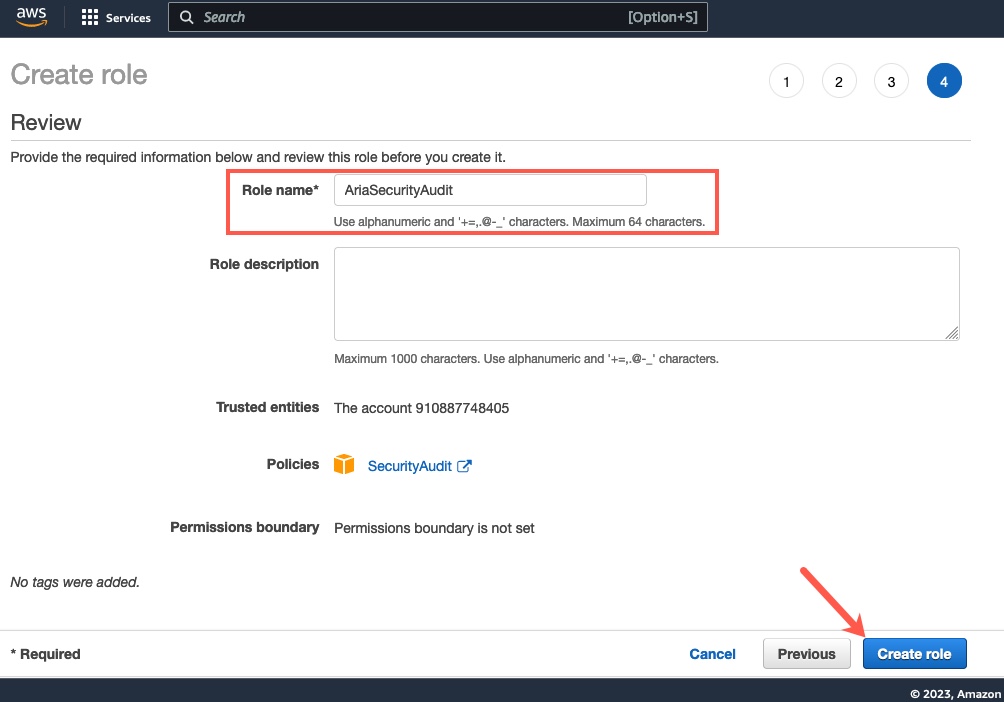
Below in the Review Screen, you will see the role name that is created “AriaSecurityAudit”, again you can change this as needed, but you will need to reference this role name later in the setup.
Click “Create Role” Button.
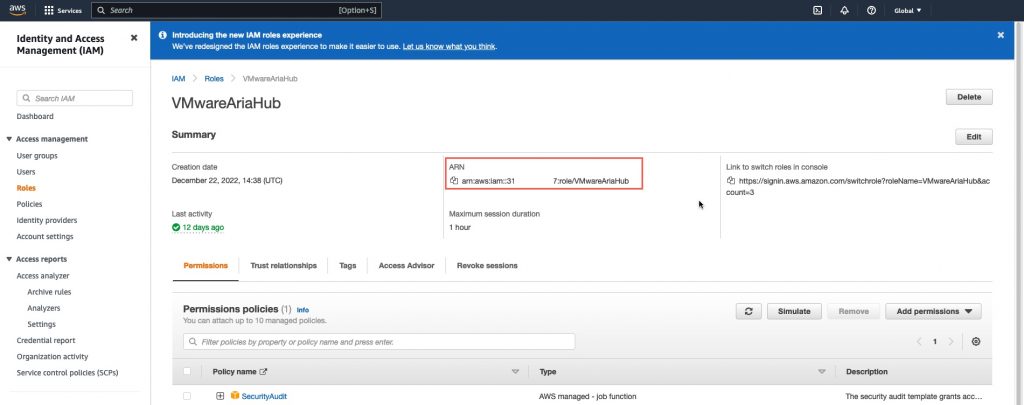
Browse the IAM Roles for the newly created role and copy the roles ARN.
Moving back to your VMware Aria Hub tab in your browser.
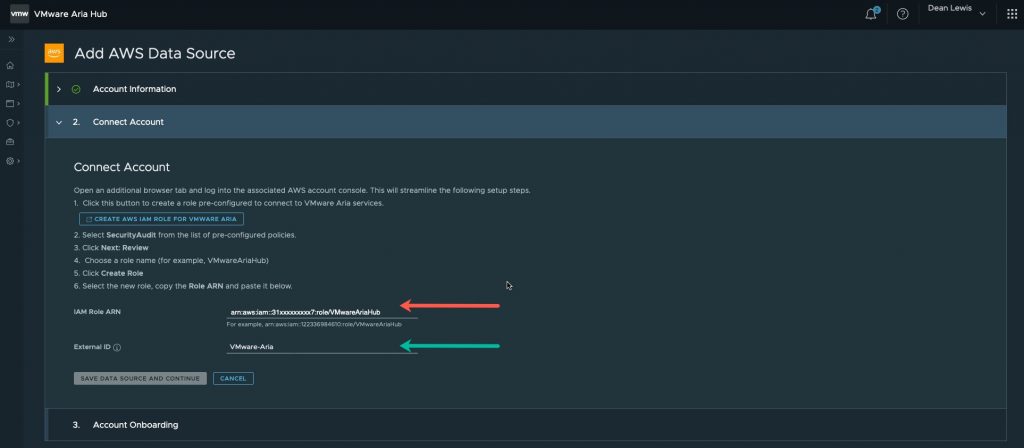
- Input the ARN you have copied from the newly created role (Red arrow)
- If you changed the External ID for the role, update as necessary (Green arrow)
Click the button “Save Data Source and Continue”.
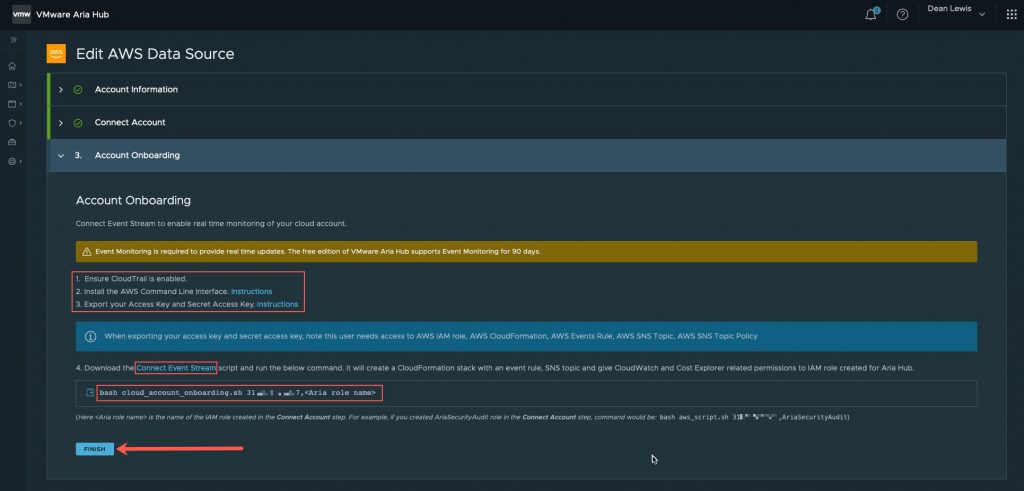
At this point your data source is configured. However, to unlock some of the powerful features of VMware Aria Hub, we need to configure the event streaming feature.
To do this, first you need to ensure:
- Your machine, or machine you have access to has the following configured:
- AWS CLI Tool
- CloudTrail is enabled in your AWS Account
- Your AWS Access Key and Secret Key are exported in your Terminal window where you will run the script from
Next download the script from the blue hyperlinked text “Connect Event Stream”, and ensure this script is executable on your system.
Run the script as the following:
bash cloud_account_onboarding.sh [account_id],[RoleName] # For Example bash cloud_account_onboarding.sh 1234567890,VMwareAriaHub
Below I’ve included both a screenshot of the script running and the output as text well.
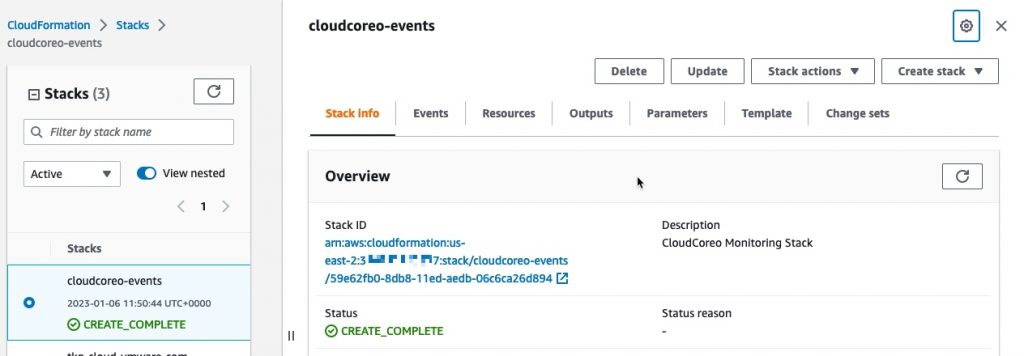
This will take a minute or two to complete running on your system. However, the setup will continue within AWS via a CloudFormation Template.
bash cloud_account_onboarding.sh 31xxxxxxxxx7,VMwareAriaHub [2023-01-04T13:58:58+0000]: INFO: Running for 1 accounts. [2023-01-04T13:58:58+0000]: INFO: Getting root account id for session's aws credentials. [2023-01-04T13:59:00+0000]: INFO: Starting onboarding process for account 31xxxxxxxxx7 [2023-01-04T13:59:00+0000]: INFO: Getting regions for account 31xxxxxxxxx7 af-south-1 ap-south-1 eu-north-1 eu-west-3 eu-south-1 eu-west-2 eu-west-1 ap-northeast-3 ap-northeast-2 me-south-1 ap-northeast-1 ca-central-1 sa-east-1 ap-east-1 ap-southeast-1 ap-southeast-2 eu-central-1 ap-southeast-3 us-east-1 us-east-2 us-west-1 us-west-2 [2023-01-04T13:59:03+0000]: INFO: Account 31xxxxxxxxx7 has a MultiRegionTrail with HomeRegion: us-west-2 ensuring policy exists: AriaHubListCloudwatchMetrics existing policy: AriaHubListCloudwatchMetrics ensuring policy exists: AriaHubGetCostingData [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region af-south-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-south-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-3 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-east-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-2 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-west-3 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ca-central-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-2 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region sa-east-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region us-west-2 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-west-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-north-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-3 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region us-west-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region me-south-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region ap-south-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-west-2 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region us-east-2 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region eu-central-1 [2023-01-04T13:59:18+0000]: INFO: Starting application of cloudformation stack for account 31xxxxxxxxx7 in region us-east-1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:22+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:23+0000]: INFO: Creating stack cloudcoreo-events with version 1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ca-central-1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-west-3 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-west-2 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-central-1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-west-1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region us-east-1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-south-1 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region us-east-2 [2023-01-04T13:59:26+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region eu-north-1 [2023-01-04T13:59:27+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region us-west-1 [2023-01-04T13:59:27+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region us-west-2 [2023-01-04T13:59:27+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region me-south-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region sa-east-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-south-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-3 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region af-south-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-1 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-northeast-2 [2023-01-04T13:59:28+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-east-1 [2023-01-04T13:59:29+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-2 [2023-01-04T13:59:29+0000]: INFO: Successfully applied cloudformation stack for account 31xxxxxxxxx7 in region ap-southeast-3 [2023-01-04T13:59:29+0000]: INFO: All accounts passed successfully.
In your AWS Console, if you browse to CloudFormation page, you’ll see an active Stack that will be running, which you can monitor the status of. Once this returns a status of “Create_Complete”. Then the configuration for VMware Aria Hub has finished.
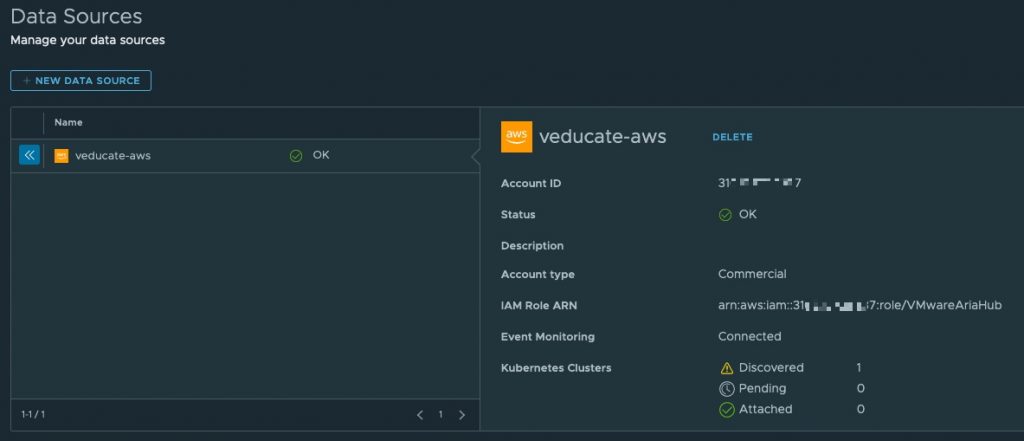
Moving back to your VMware Aria Hub browser tab, on the Data Sources page, you’ll see that the account status should be “OK” with a green tick.
Exploring the VMware Aria Hub Interface
Obviously, the recording at the start of the blog will take you through a walk-through of the interface, but I thought it was worth while calling out a few points about the interface and features. Once you are receiving data into VMware Aria Hub, you can expect the following:
- Full Inventory of your cloud resources, with relationship topology mapping:
- For example, see how EC2 instances are connected to S3 buckets, Key Pairs and Load Balancers.
- Extensive querying capabilities via both the UI and API
- Take a look at this page for some examples
- Current Cost information for your deployed resources
- Security information aligned to the CIS Benchmark for your Public Cloud
- In my example, I noticed that the default configurations to deploy EC2 instances mean I have a lot of unencrypted EBS volumes!
- Business application classification and mappings
- VMware Aria Hub will start to use smart logic to group resources together into application groupings, such as those sat behind a load balancer.
- Create your own Application groupings
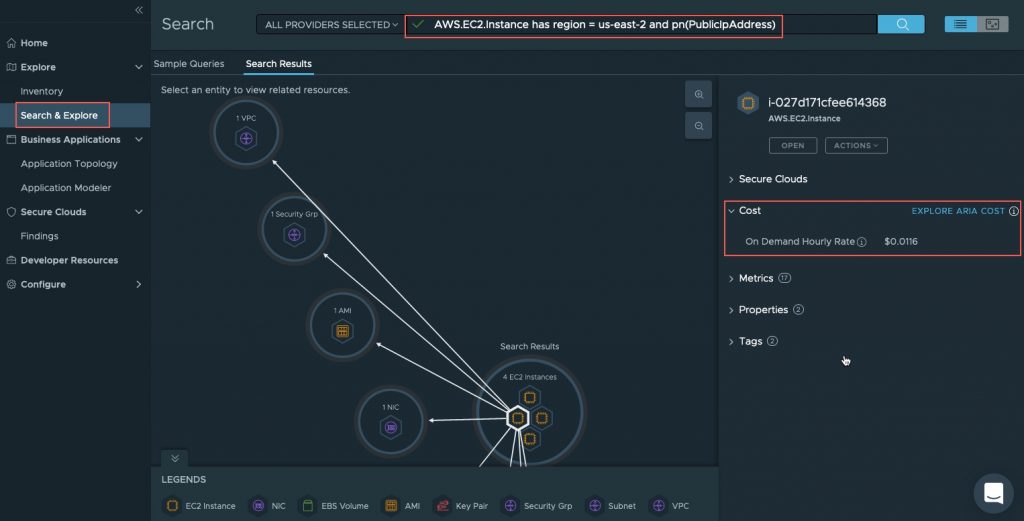
In the below screenshot, I’ve run a query to find all EC2 instances which are configured with a public IP address.
- I can see the associated costs for each EC2 instance that I select
- By selecting a returned EC2 instance, the topology view shows me any related resources to that object.
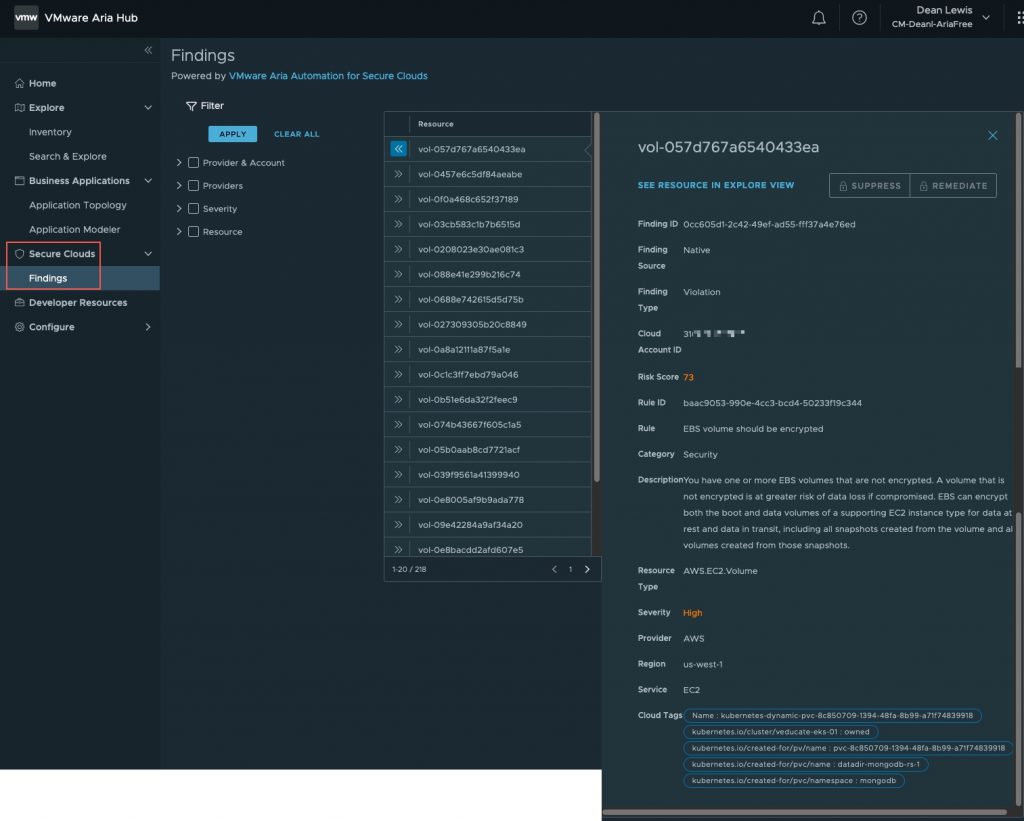
Under the Secure Clouds section, I can see all the findings across my monitored environments. Alternatively, for each object I’m viewing in the Explore UI (as above), I can expand the “Secure Clouds” component to see if there is any violations linked for that particular object.
In the below example, we can see my EBS volume is not encrypted, with details of the rule that was triggered. We can even see the tags, which in this case, show further information to identify where this volume is used, it’s my MongoDB application running inside my EKS cluster!
Because we are using the Aria Hub Free Tier, the suppress and remediate options are unable, but can be unlocked by purchasing VMware Aria Automation for Secure Clouds.
Wrap-Up
It’s quick and easy to get the VMware Aria Hub Free Tier setup, and for an additional tool to provide visibility into your public cloud environments, it’s a no-brainer, it’s free! I can’t wait to see the power of the full product where you can connect all the Aria (vRealize) products, as well as VMware vSphere environments. Having a single point of entry to query information about all your systems will be so powerful! There’s also future features coming such as Business Insights, running analytics, AI and ML on all of that data for you to provide an insight into your platform. And migration service assessment, planning and execution.
I did not labour too much in writing an exploration of the VMware Aria Hub features in this blog post, mainly because I cover them in the recording at the start of this blog post. I felt that it was a better way to show off those features once the data is available in the UI!
For everything else VMware Aria Hub, head over the documentation pages for more use-cases and examples:
Regards