In this blog post, I will cover the steps for an air-gap installation for Kasten K10. For situations where your Kubernetes cluster doesn’t have available internet access to pull down the container images directly from their online locations.
Pre-requisites
- Image Registry that is accessible by your Kubernetes cluster
- In this example I am using the Harbor Image Registry.
- Client that has access to download the container images and then to the Image Registry
- In this example, I am using my local machine which has docker installed.
- Helm downloaded
- Run the following to get the helm files locally for the install.
helm repo update && \ helm fetch kasten/k10 --version=<k10-version> Example for Kasten K10 4.5.0 helm repo update && \ helm fetch kasten/k10 --version=4.5.0 This will download a file, for example "k10-4.5.0.tgz"
Log into your Image Registry
First you need to ensure that your docker client (or similar) has authenticated to your Image Registry which your air-gap Kubernetes cluster can access.
When using Harbor and Docker, I typically use this method with a robot account for programmatic access.
However, when running the Kasten tooling which we’ll discuss next, I kept hitting an error.
54e42005468d: Waiting File=kasten.io/k10/kio/tools/k10offline/k10offline.go Function=kasten.io/k10/kio/tools/k10offline.PushK10Images Line=179 hostname=3ffc0162e190
Error: {"message":"Failed to push K10 container images to harbor-repo.veducate.co.uk/deanl","function":"main.pullImages","linenumber":171,"cause":{"message":"Failed to push","function":"kasten.io/k10/kio/tools/k10offline.PushK10Images","linenumber":181,"fields":[{"name":"image","value":"harbor-repo.veducate.co.uk/deanl/kanister-tools:k10-0.69.0"}],"cause":{"Stderr":"dW5hdXRob3JpemVkOiB1bmF1dGhvcml6ZWQgdG8gYWNjZXNzIHJlcG9zaXRvcnk6IGRlYW5sL2thbmlzdGVyLXRvb2xzLCBhY3Rpb246IHB1c2g6IHVuYXV0aG9yaXplZCB0byBhY2Nlc3MgcmVwb3NpdG9yeTogZGVhbmwva2FuaXN0ZXItdG9vbHMsIGFjdGlvbjogcHVzaAo="}}}
Base64 decode the message above in light bold provides you the response:
unauthorized: unauthorized to access repository: deanl/kanister-tools, action: push: unauthorized to access repository: deanl/kanister-tools, action: push
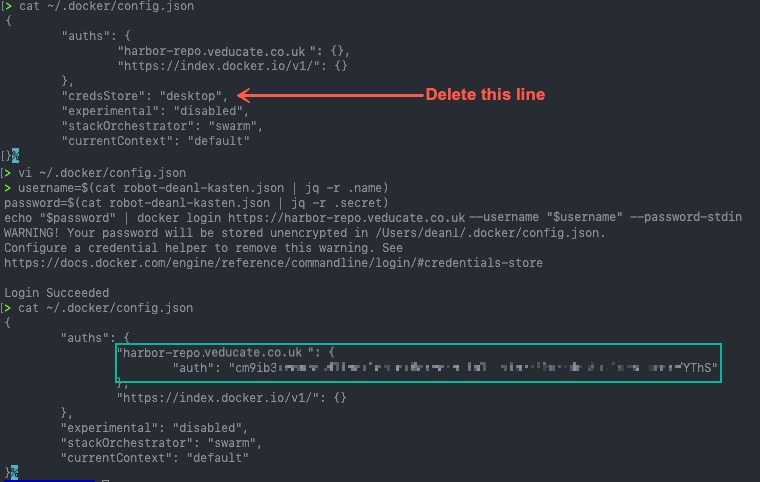
To resolve this, I had to remove the credsStore line from my ~/.docker/config.json file. Then log into my Harbor registry using the above method.
- This does mean your auth account details are stored in a JSON file locally.
Pull down the Kasten K10 images locally and Push to internal Air-Gap Image Registry
Kasten has provided an easy-to-use tool which can run locally on your docker client to make pulling the necessary images simple.
docker run --rm -ti -v /var/run/docker.sock:/var/run/docker.sock \
-v ${HOME}/.docker:/root/.docker \
gcr.io/kasten-images/k10offline:{TAG} pull images
# Example with Tag
docker run --rm -ti -v /var/run/docker.sock:/var/run/docker.sock \
-v ${HOME}/.docker:/root/.docker \
gcr.io/kasten-images/k10offline:4.5.0 pull images
By specifying the appropriate tag, you this will use a container image to pull down all the containers and store them within your docker client. To push to an internal repo, you simply add the argument:
--newrepo {repo url}
For example:
docker run --rm -ti -v /var/run/docker.sock:/var/run/docker.sock \
-v ${HOME}/.docker:/root/.docker \
gcr.io/kasten-images/k10offline:4.5.0 pull images --newrepo harbor-repo.veducate.co.uk/deanl
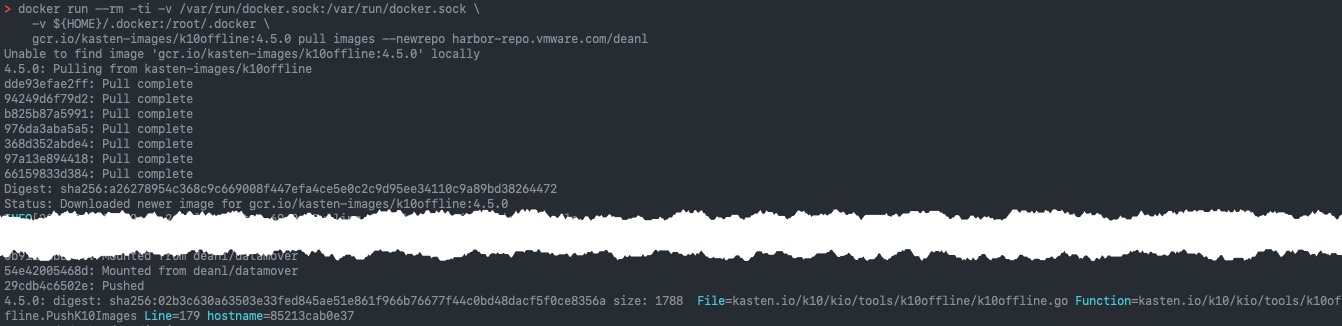
The below image shows the tool download containers and pushing them to the repo.
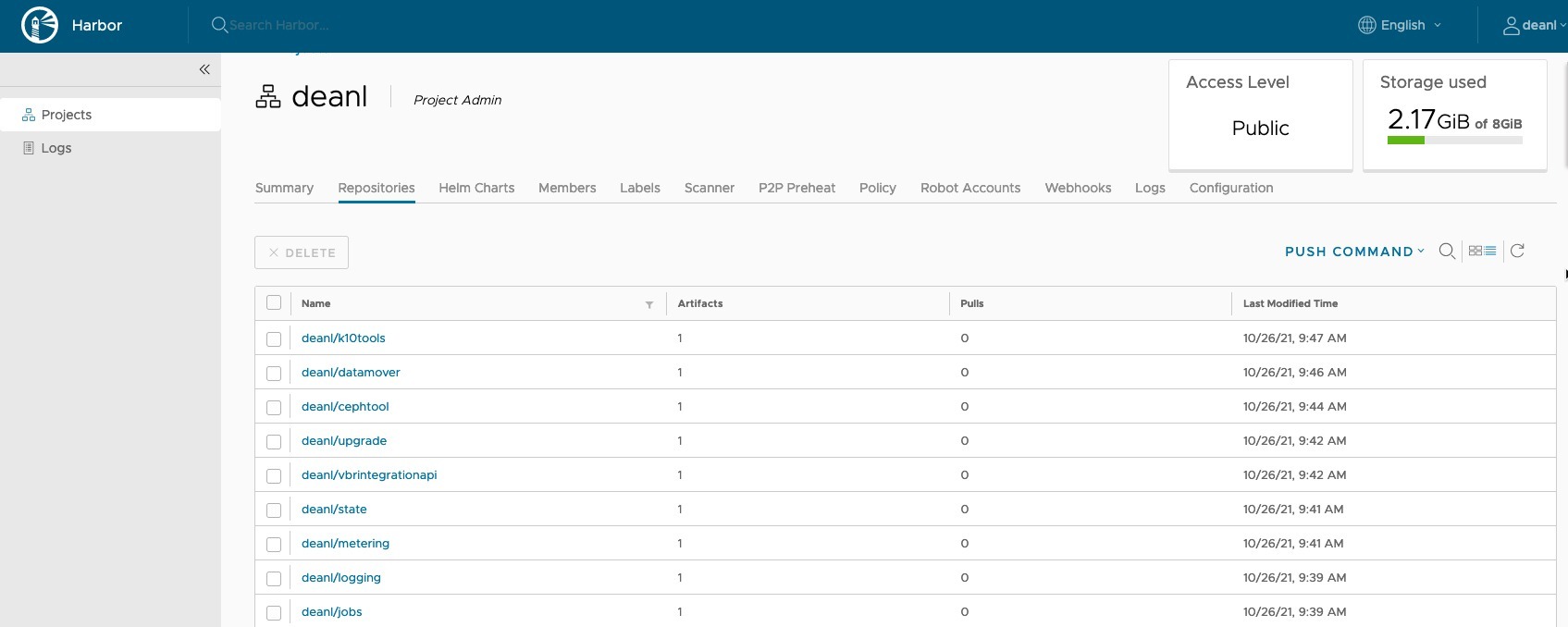
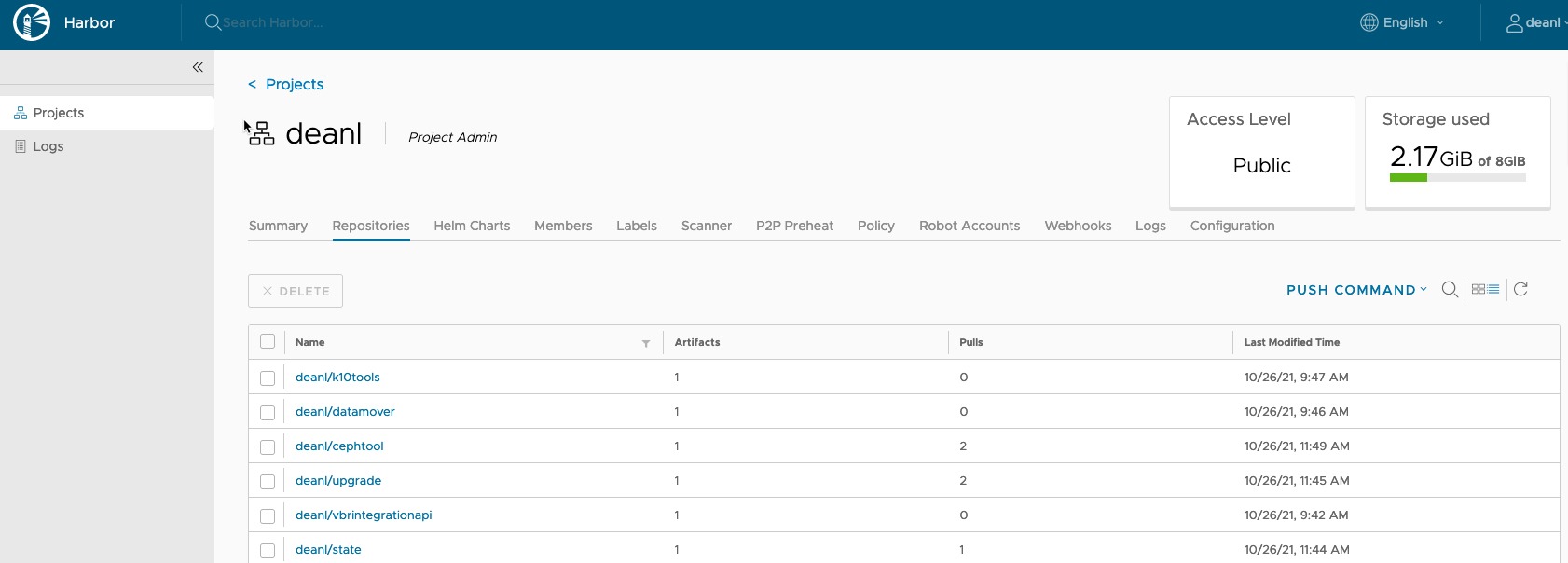
Here are my images in Harbor.
Installing Kasten K10 with a local Helm Chart and Container Images
Create your Kasten namespace
kubectl create namespace kasten-io
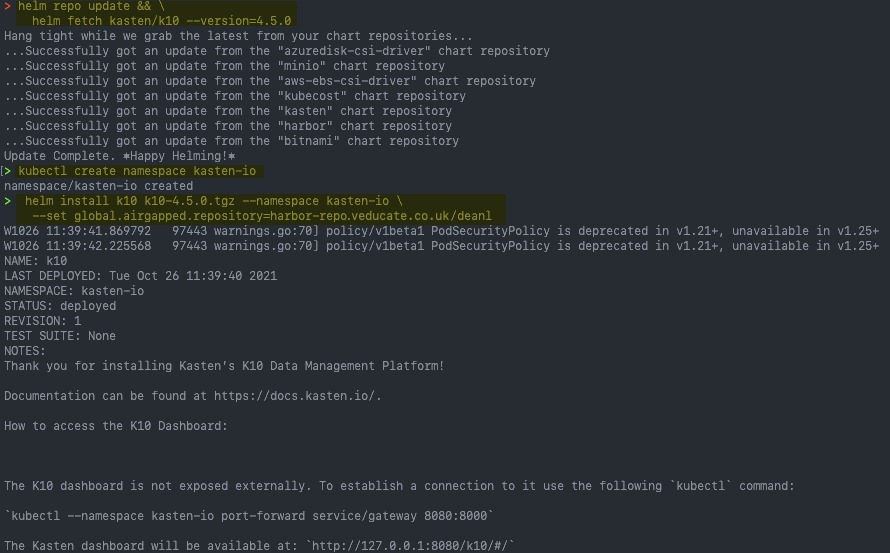
Then run the following Helm command
helm install k10 k10-4.5.0.tgz --namespace kasten-io \
--set global.airgapped.repository={registry URL}
# Example
helm install k10 k10-4.5.0.tgz --namespace kasten-io \
--set global.airgapped.repository=harbor-repo.veducate.co.uk/deanl
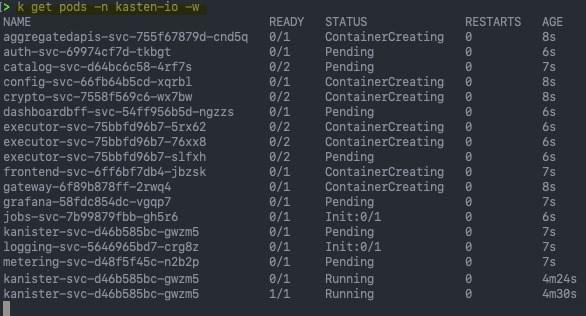
We can now watch the pods start by using the command:
kubectl get pods -n kasten-io -w
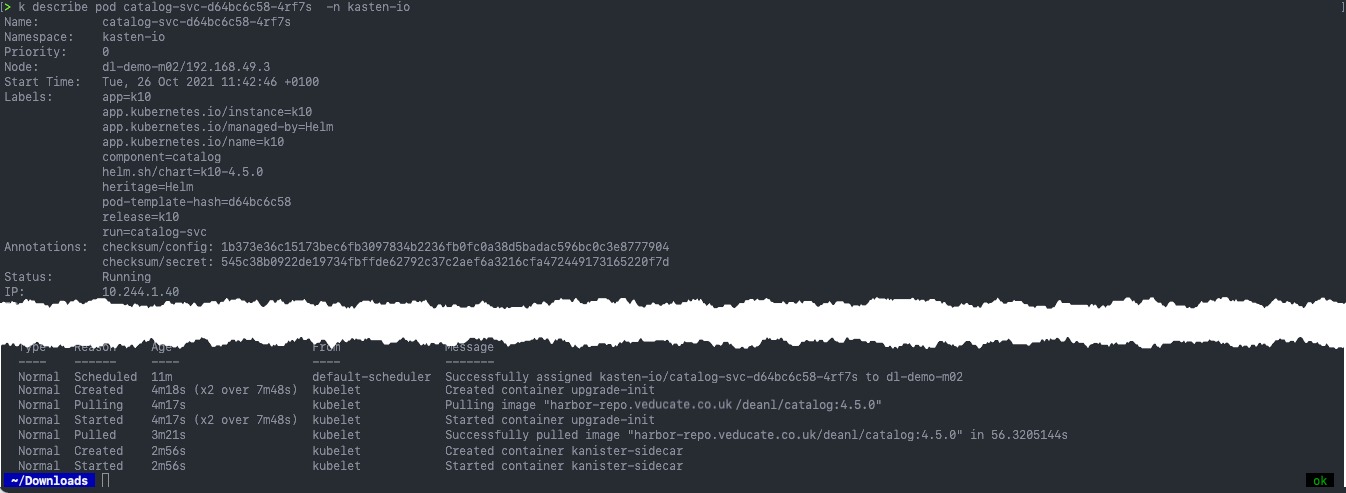
We can check these are coming from our local image repository by running the describe command against one of our pods.
Finally, we can also see pulls in our Harbor image registry as well.
Summary
Kasten has made it easy to perform an air-gap internet restricted installation of their software in a Kubernetes cluster, made especially easy thanks to the little k10offline tool you run in your docker client to grab the necessary images for you.
I did hit that little authentication issue where I had to remove the credsStore in docker, due to the way the tool reads the Image Registry auth details. I messaged the Kasten support team about this and they were quick to give me the workaround I documented earlier.
I’m not going to say outside of this I did anything more than follow the Kasten docs on the subject. But I always feel sometimes it’s good to add some more context and colour with screenshots and using real environments to demonstrate these capabilities and configurations.
Regards