Just a quick blog on how to get the Data Protection feature of Tanzu Mission Control on Red Hat OpenShift. By default you will find that once the data protection feature is enabled, the pods for Restic component of Velero error.
- Enable the Data Protection Feature on your Openshift cluster
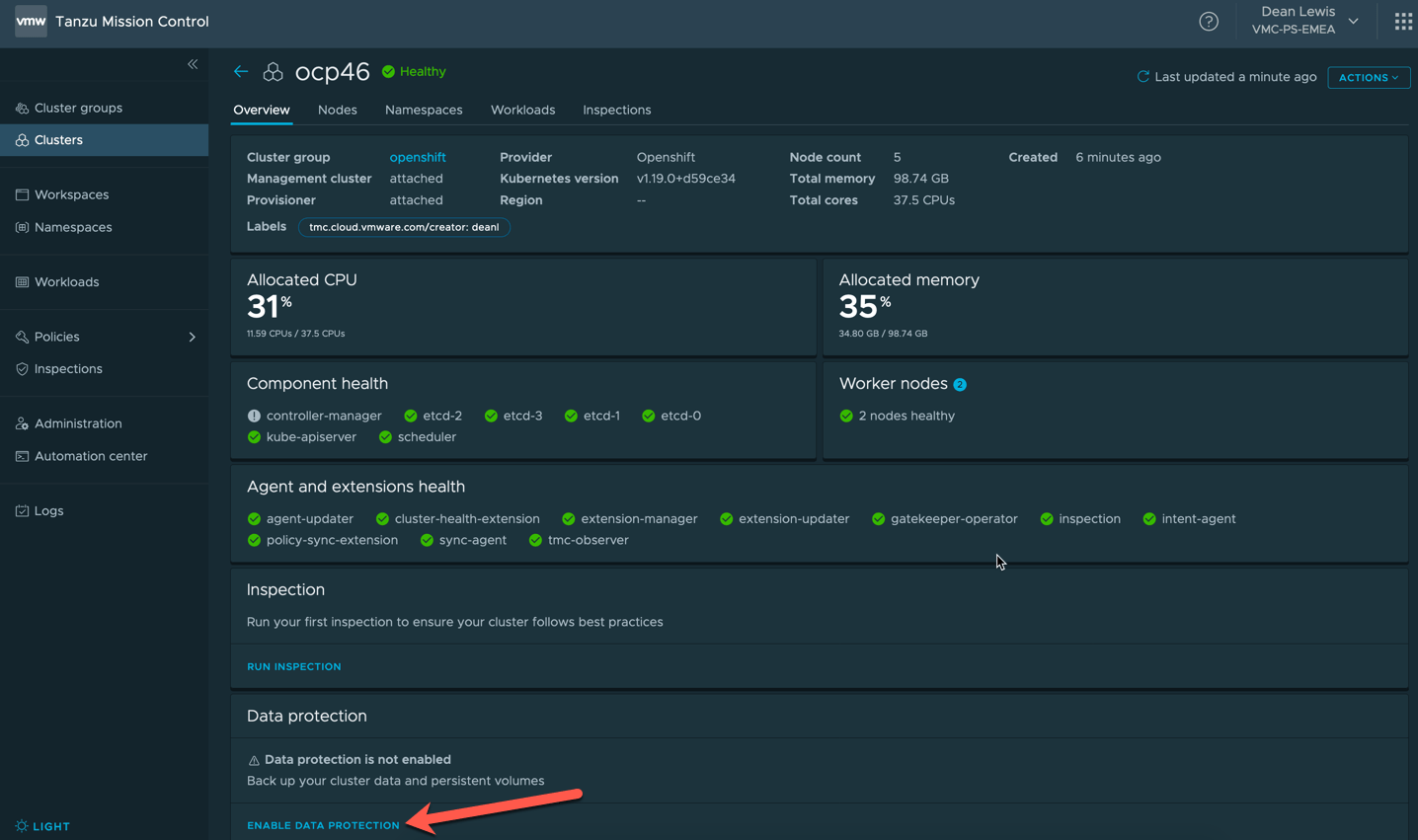
- You will see the UI change to show it’s enabling the feature.
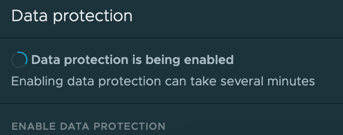
- You will see the Velero namespace created in your cluster.
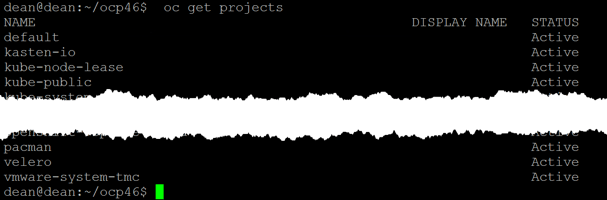
However the “Data Protection is being enabled” message in the TMC UI will continue to show without user intervention. If you show the pods for the Velero namespace you will see they error.
This is because OpenShift has a higher security context out of the box for containers than a vanilla Kubernetes environment.
The steps to resolve this are the same for a native install of the Project Velero opensource install to your cluster.
- First we need to add the velero service account to the privileged SCC.
oc adm policy add-scc-to-user privileged -z velero -n velero
![]()
- Secondly we need to patch the DaemonSet to allow the containers for Restic run in a privileged mode.
oc patch ds/restic \
--namespace velero \
--type json \
-p '[{"op":"add","path":"/spec/template/spec/containers/0/securityContext","value": { "privileged": true}}]'
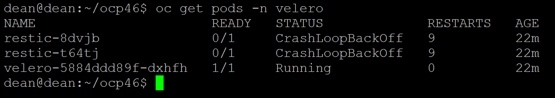
After this, if we run the command to get all pods under the Velero namespace again, we’ll see that they are replaced with the new configuration and running.
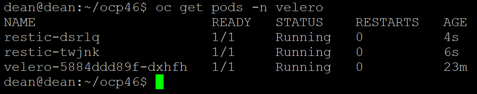
Going back to our TMC Console, we’ll see the Data Protection feature is now enabled.
Regards

do you have any article how id you register Openshift Cluster with Tanzu Mission Control
You attach the cluster the same as any other.
https://docs.vmware.com/en/VMware-Tanzu-Mission-Control/services/tanzumc-using/GUID-6DF2CE3E-DD07-499B-BC5E-6B3B2E02A070.html