As part of some internal lab work, I had to move the user objects with their passwords to a new forest. It was key to migrate the passwords to ensure that disruption to the users was minimized.
To migrate the users, I used the Microsoft Active Direction Migration Tool (ADMT + documentation) alongside the Password Migration Service.
In this blog post I am going to cover;
- Create connectivity between both AD Forests
- Installing the ADMT software + Password Migration Service
- Creating a user list for migration
- Migrating User objects + Passwords between AD Forests
Create connectivity between both AD Forests
There must be IP network connectivity between the DC’s in your Forests.
DNS setup
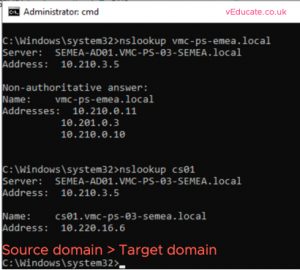
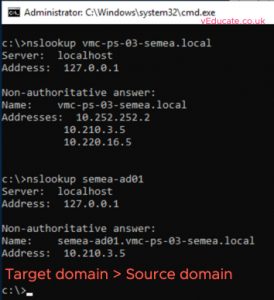
You need to configure conditional forwarders between your forests, so they can resolve one another.
On the source domain controller;
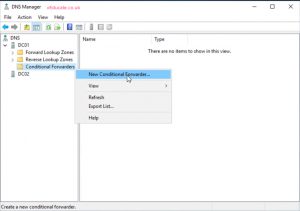
- Open up the DNS console, and right click the Conditional Forwarder folder to create a new record.
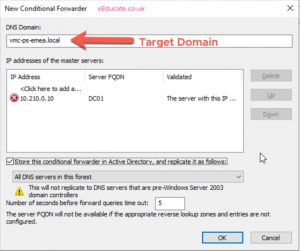
- Enter your target domain name and IP address/es of your domain controllers in the target domain. Select “store this conditional forwarder in active directory”, to replicate to other DCs in the source domain.
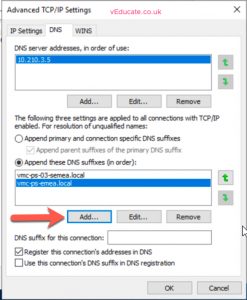
It is also a good idea to add the target domain DNS suffix to your Source DC network adapter, this allows for short name resolution.
Repeat the same steps on the target domain controllers, pointing the conditional forwarder to your source domain.
After this, ensure you can successfully look up the domains from another with the correct Domain controller IP addresses being returned. Also check short name resolution works.
Create Active Directory Forest Two-Way Trust
Next you need to create a forest trust
- You can read about the different options here
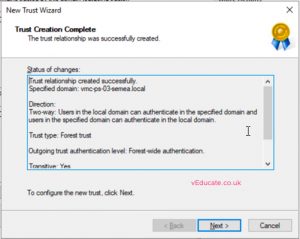
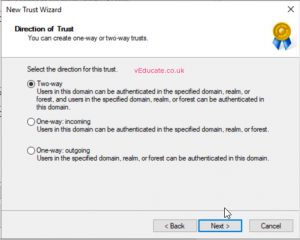
I will create a two-way forest trust which means we are able to authenticate users between domains, and this trust will be removed after I’ve migrated the users.
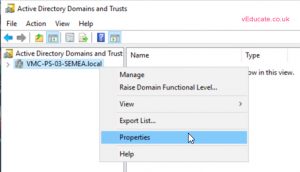
On the source domain controller
- Open Active Directory Domains and Trusts. right click your domain name and go to properties
- Click the trusts tab, and click the new trust button
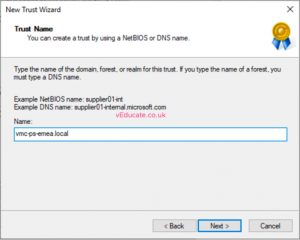
- Enter the name of your target domain
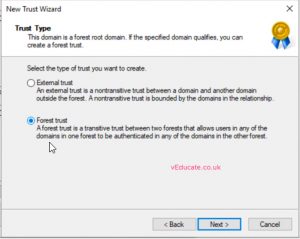
- Select forest trust
- Select two-way trust
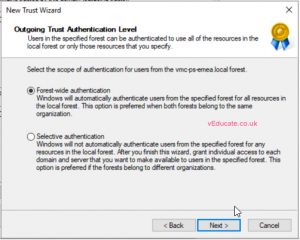
- Select forest wide trust
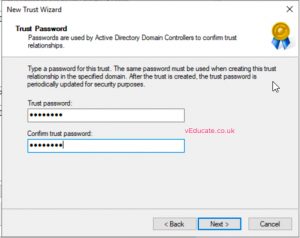
- Enter trust password (you will use this when you create the trust on the target domain side)
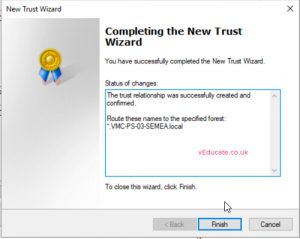
- Click next x2
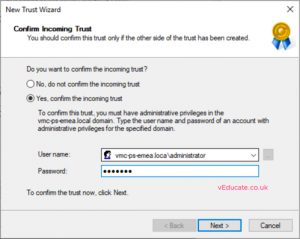
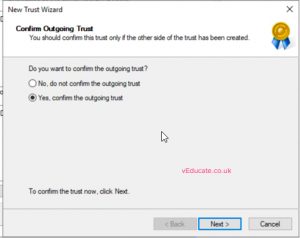
- If you click to confirm the trust at this point, it will fail as it does not exist on the target domain side yet. (See screenshots)
Installing the ADMT software
Install this on your Target domain controller, or a machine in target domain. There is a requirement for an SQL server to host a database. I used SQL Express for the lab setup.
Installing the Password Migration Service
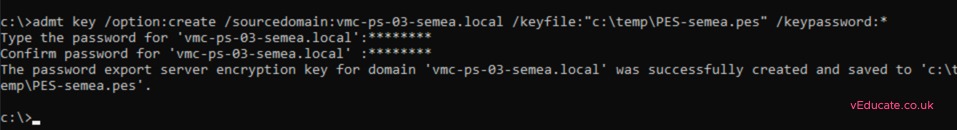
First you must generate an encryption key from a DC in your target domain. Open CMD as administrator and run;
admt /key option:create /sourcedomain:{source domain name} /keyfile:{folder path to save the file} /Keypassword:*
Using * for the pwd flag, will then prompt you for the password when the command is run
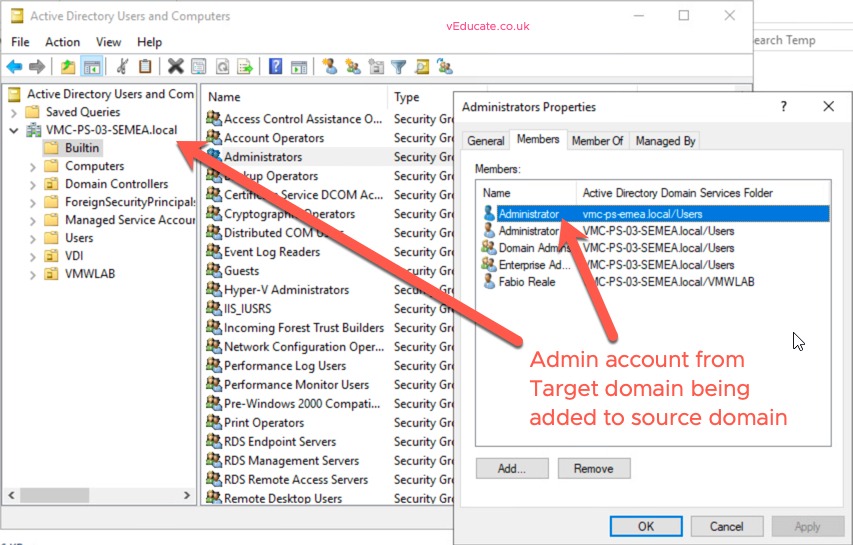
On your source domain, in the built-in Administrators group, add in the domain administrator from your target domain.
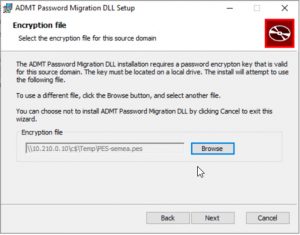
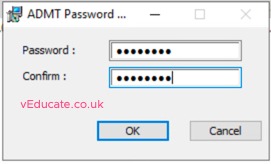
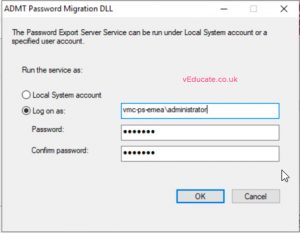
On the domain controller in your source domain, install the Password Migration Service.
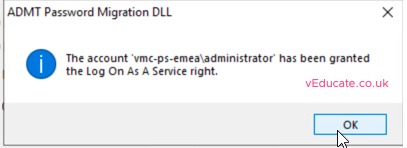
When prompted, install the service as the domain admin from your target domain, this account will be added the log on as service right.
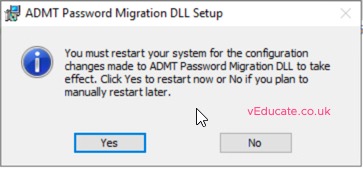
A reboot of the machine where this service is installed will be needed.
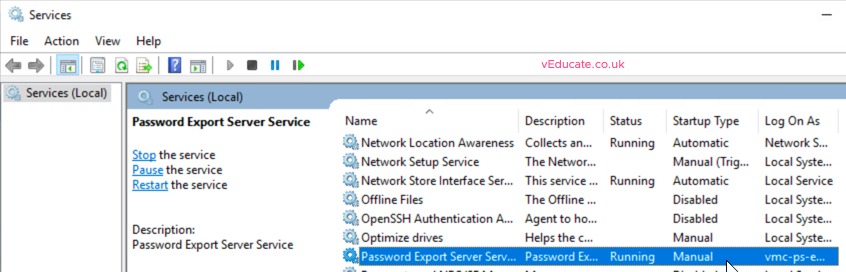
After the reboot, you will need to manually start the “Password Export Server Service”, after you’ve migrated your users, for security, you should stop this service.
Creating a user list for migration
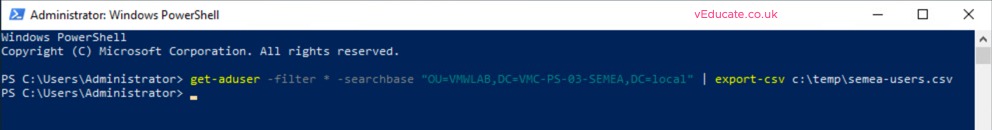
The last step before migration, is creating a CSV file with a list of the users we want to migrate. I will do this using a simple PowerShell command
get-aduser –filter * -searchbase {OU full path} | Export-csv {path}
You can be more complex if you need to target users who are part of a security group or multiple OUs.
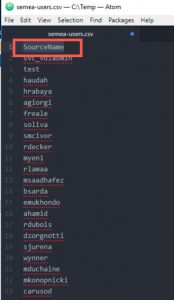
You will need to edit this CSV to use the accepted headers for use as an “include file” for ADMT. You can follow the official documentation for these headers.
Migrating users between AD Forests
Ok, we’ve finished the prep work. Now time to migrate the users.
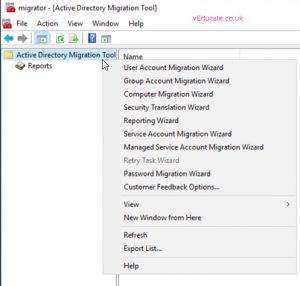
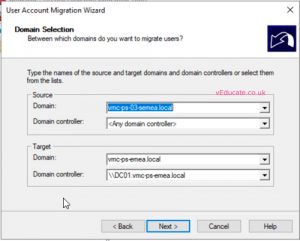
- Open up ADMT console, right click on the Migration tool folder and select “User Account Migration Wizard”
- Type in your source domain, and select your target domain from the drop down
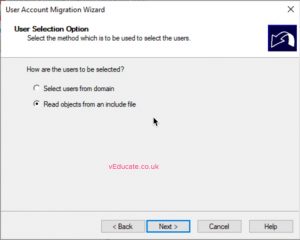
- Select the option “read objects from include file”
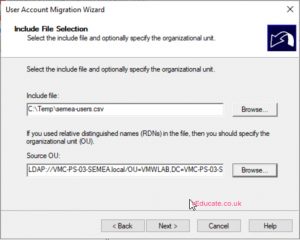
- Set your include file location and Source OU where your users are located
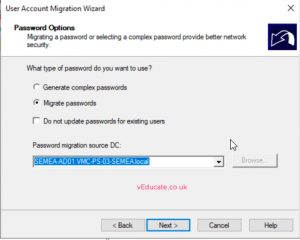
- Select the option to migrate the user’s passwords
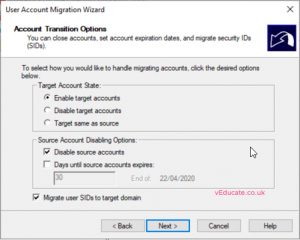
- Select account options for after the migration
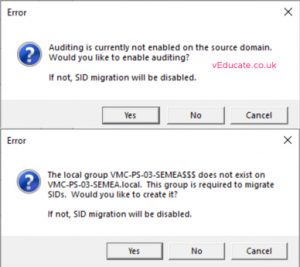
- If selected SID History Migration, accept the options
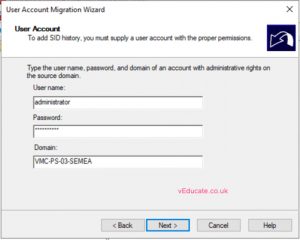
- Input the domain admin detail to authenticate to the Source Domain
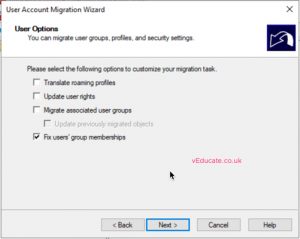
- Configure user options for after the migration
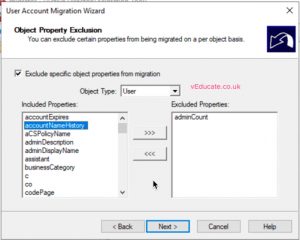
- Select any user object attributes you do not want to be migrated
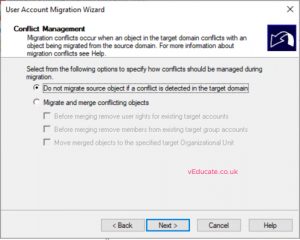
- Select your option for how to handle user conflicts
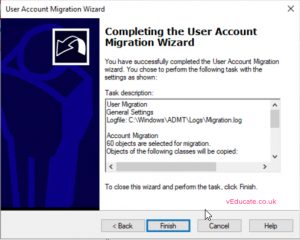
- Complete the user migration wizard
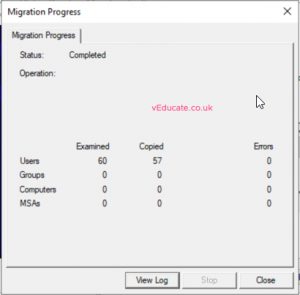
- Watch the progress, you also have easy access to view the logs from here
- Configure user’s password so that they do not need changing upon next login.
get-aduser -filter * -searchbase {OU path} | set-aduser -changepasswordatlogon $false
Hope this helps someone out there, I recommend that you read the ADMT document first before undertaking a migration of AD users in production, and then test in a lab environment.

Thanks for sharing, good article.
Do you know if there is a way to migrate password history? My customer is migrating to a new forest but needs to ensure that users do not use any of their prior 12 months of passwords.
Hi, I’ve had a look, and this functionality is not available with ADMT, also looking at third party tools for these operations, none of them look to support migrating password history. So I think this is not possible.
Hello
Where can i get ADMT and PMS, those are not available from Microsoft site?
Here you go;
https://support.microsoft.com/en-ie/help/4089459/download-locations-and-support-information-for-admt-and-pes
Awesome work!
Has been a great help to me…
We are doing a hardware refresh (old stack to new stack). So, the DC’s are named the same. How do we make this work for migrating objects and passwords from AD01 to AD01? Thanks.
So if your moving from ad01.olddomain.local to ad01.newdomain.local – this shouldn’t be an issue, it should work as described. If you are moving from ad01.domain.local to ad01.domain.local, then well I doubt this is even possible, because you know, everything is the same name.
I once moved domains from something.domain.local which was the full domain name at root in that forest. To a brand new AD forest called domain.local, and that took a lot of messing around with DNS records on both sides of the domains, to get a one-way trust working, and was probably highly unsupported from a connectivity point of view.