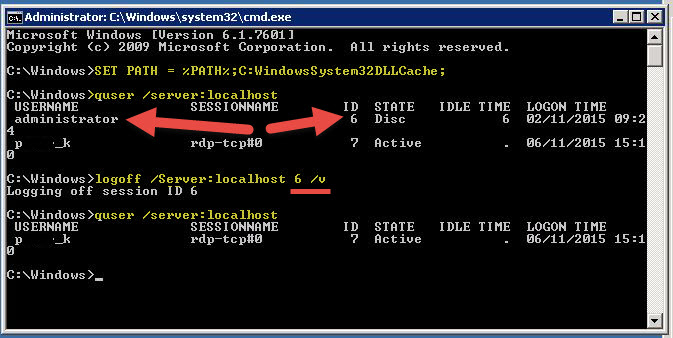
The Issue
Users password has expired
When logging onto a Wyse Client (in this case a C10LE or Dx0D running the latest firmware), you are told your password has expired. You are given the option to change your password, once you click OK, you are presented with the following message;
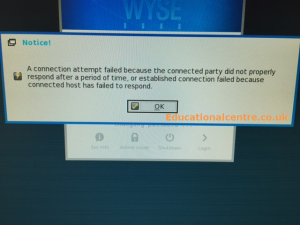
The Cause
Turning on Verbose mode on the Storefront server and running Microsoft DebugView Tool to view the output files (C:\Program Files\Citrix\Receiver Storefront\Admin\Trace)
Here is the Citrix KB on setting up verbose logging and reading the trace files.
Add-PSSnapin Citrix.DeliveryServices.Framework.Commands
Set-DSTraceLevel –All –TraceLevel Verbose
Get-Service "CitrixConfigurationReplication" | Restart-Service
Get-Service "CitrixCredentialWallet" | Restart-Service
Get-Service "CitrixDefaultDomainService" | Restart-Service
Get-Service "CitrixSubscriptionsStore" | Restart-Service
Get-Service "Citrix Peer Resolution Service" | Restart-Service
Set-DSTraceLevel –All –TraceLevel Off
- In the debug we could see that when the password reset tokens were sent;
[21620] <?xml version="1.0" encoding="UTF-8"?><!DOCTYPE AdminProtocol SYSTEM "Admin.dtd">test.user</UserName><Domain type="NT">STUDENT</Domain><OldPassword>oranges</OldPassword><NewPassword>apples</NewPassword></RequestChangePassword></AdminProtocol>
Here you can make out that the above highlighted words are the user credentials and the old and new password.
- There was a response stating;
[21620] PnaAuthenticationLogic: Authenticate response status: FailedInvalidDomain, isSuccess: False, password expired: False
- We also seen a “Charlotte” error as well;
[21620] PnaAuthenticationExplicitController: PnaAuthenticationException from change password Citrix.DeliveryServices.PnaProtocol.Authentication.PnaAuthenticationException: CharlotteErrorBadCredentials
Below is a dissection of the debug output;
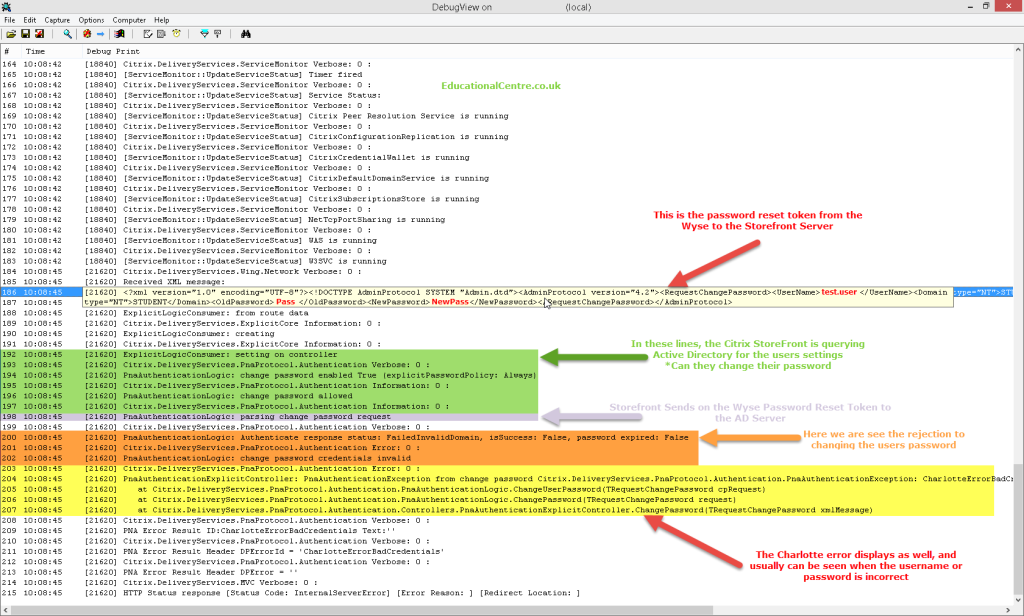
The Fix
The fix was to change the Wyse configuration file (WNOS.ini) for the line that puts in the available domains to the FQDN rather than the NETBIOS name for each domain.
Our old configuration was;
- DomainList=”Student,Admin”
Our new configuration was;
- DomainList=”Student.educationalcentre.co.uk,Admin.educationalcentre.co.uk”
We could then see that in the debug file, the line describing the domain details, includes the FQDN.
<Domain type="NT">STUDENT.Educationalcentre.co.uk</Domain>
This issue was not apparent when using Citrix XenDesktop 5.5 and Citrix Web Interface, only when we migrated to XenDesktop 7.6 and StoreFront Services, which I imagine uses a higher level of security, meaning passing the NETBIOS name through is unacceptable now.
Regards
Dean