Kubernetes is a platform which is starting to lose the need for introduction in most settings. However, it still can be a complex beast to get to grips with, and getting your infrastructure components configured correctly is key to providing a successful Kubernetes environment for your applications.
One of these such areas is storage.
- Remember the days of performance testing your iSCSI or Fibre Channel SANs for your virtualisation platform?
- Creating storage based policy management objects in vCenter for your SANs capabilities
- Integrating your backup solution to use storage snapshots.
With your Kubernetes platform, you need to ensure a correct storage configuration, and benchmark your storage performance, like you would with any other platform. Then test the container storage features such as snapshots of the persistent volumes.
The configuration for each vendor when integrating with Kubernetes will be different, but the outcomes should be the same.
What is Kubestr?
Enter Kubestr, the Open-Source project tool from Kasten by Veeam, designed to help with ensuring your storage is configured correctly, help you benchmark the performance and test features such as snapshots.
Getting started with Kubestr
Simply Download Kubestr for the platform you wish to run the tool from. For me I’ll be running it from my Mac OS X machine, which has connectivity to my Kubernetes platform (AWS EKS, I used this blog to create it).
I extracted the zip file and have the Kubestr command line tool available in the output folder.
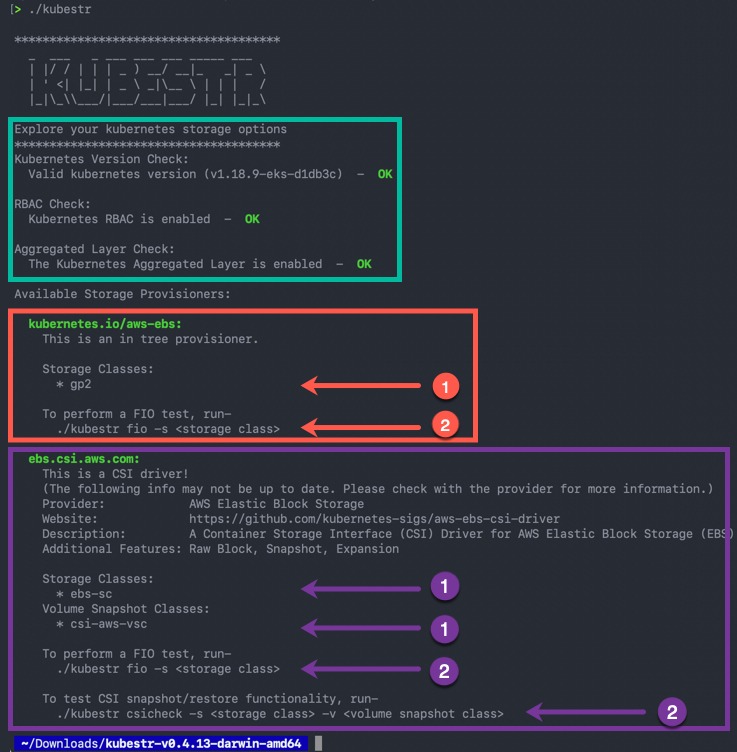
Running the tool for the first time will run some tests and output a number of useful items of information on how we can use the tool. Which I will start to breakdown as we continue.
For Kubestr to run, it will use the active context in your kubectl configuration file.
Green Box – we have our initial checks.
- Kubernetes version
- RBAC check
- Kubernetes Aggregated layer check
Then we have the details from our available storage provisioners that are installed for our cluster. You can see what I have two installed. Continue reading Kubestr – Open-Source Kubernetes Storage benchmarking tool