In this blog post we will cover the following topics
- Tanzu Mission Control - - Workspaces - - - Creating a workspace - - - Creating a managed Namespace - - - Viewing a managed Namespace - - Policy Driven Cluster Management - - - Creating a Image Registry Policy - - - Creating a Network Policy
The follow up blog posts are;
Tanzu Mission Control - Getting Started Tanzu Mission Control - Cluster Inspections - Workspaces and Policies - Data Protection - Deploying TKG clusters to AWS - Upgrading a provisioned cluster - Delete a provisioned cluster - TKG Management support and provisioning new clusters - TMC REST API - Postman Collection - Using custom policies to ensure Kasten protects a deployed application
Workspaces
Workspaces provide an application view, where you logically group Kubernetes Namespaces together, regardless of the cluster to which they are attached.
This is in contrast to Cluster Groups, which are focused on the infrastructure view.
These Workspaces can be created to align to your projects or applications, from a hierarchy point of view, you would then authorize your users to these Workspaces, so that they can monitor and manage the namespaces related to their function.
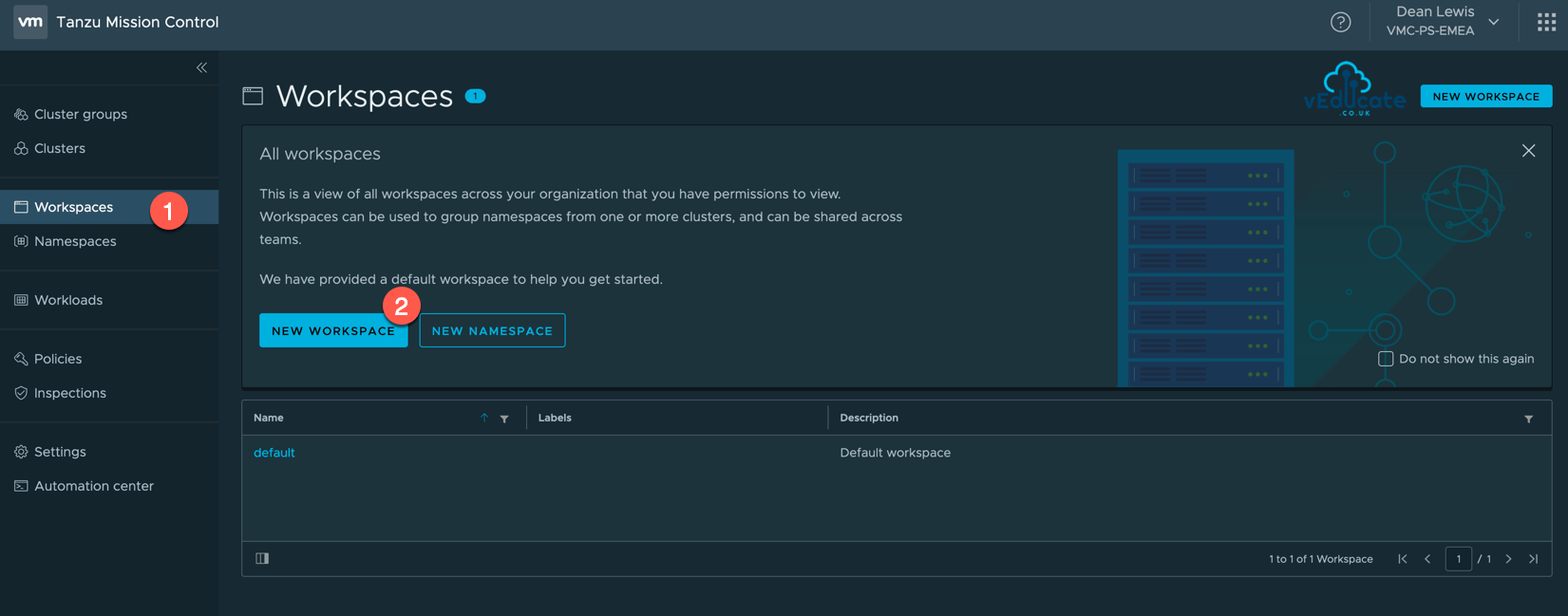
Creating a Workspace
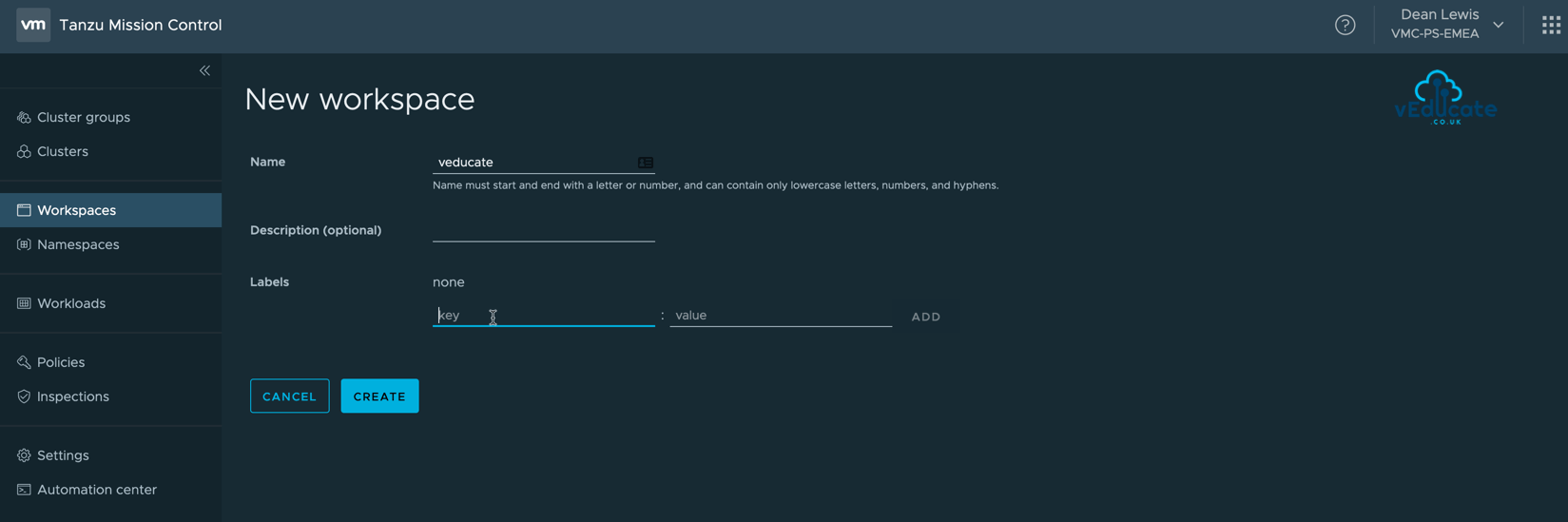
Click the Workspace navigation view on the left-hand side, and then New Workspace.
Specify your Workspace name, and provide the optional description and labels, these can be added after creation if needed.
Now you have a Workspace, it’s no good without any associated Namespaces, so let’s continue.
Creating a managed Namespace
All Namespaces attached to a Workspace will be managed Namespaces under TMC.
To create a managed Namespace, you can do this in one of four places;
- Within the Workspace Navigation view
- Inside the Workspace Object itself
- On the Namespace Navigation view
- On the Cluster Object > Navigation Tab
Continue reading VMware Tanzu Mission Control – Workspaces and Policies