In this blog post we will cover the following topics
- Tanzu Mission Control - - Cluster Inspections Overview - - What Inspections are available - - Performing Inspections - - Viewing Inspections
The follow up blog posts are;
Tanzu Mission Control - Getting Started Tanzu Mission Control - Cluster Inspections - Workspaces and Policies - Data Protection - Deploying TKG clusters to AWS - Upgrading a provisioned cluster - Delete a provisioned cluster - TKG Management support and provisioning new clusters - TMC REST API - Postman Collection - Using custom policies to ensure Kasten protects a deployed application
Cluster Inspections Overview
This for me is one of the best features of Tanzu Mission Control, and an area which I expected will be developed further in the future.
Cluster inspections provide a point-in-time report of the condition of the cluster, you might want to run them periodically (to avoid drifting out of conformance) and any time you make significant alterations, such as after you patch or upgrade a cluster.
This capability is achieved by using Sonobuoy, an open source community standard, which provides diagnostics of your Kubernetes environments through conformance testing and additional plugins.
What Inspections are available?
The following cluster inspections are available from the Overview and Inspection tabs of the cluster detail page in the Tanzu Mission Control console.
- Conformance inspection;
Validates the binaries running on your cluster and ensures that your cluster is properly installed, configured, and working. You can view the generated report from within Tanzu Mission Control to assess and address any issues that arise. For more information, see the Kubernetes Conformance documentation at https://github.com/cncf/k8s-conformance/tree/master/docs.
- CIS benchmark inspection;
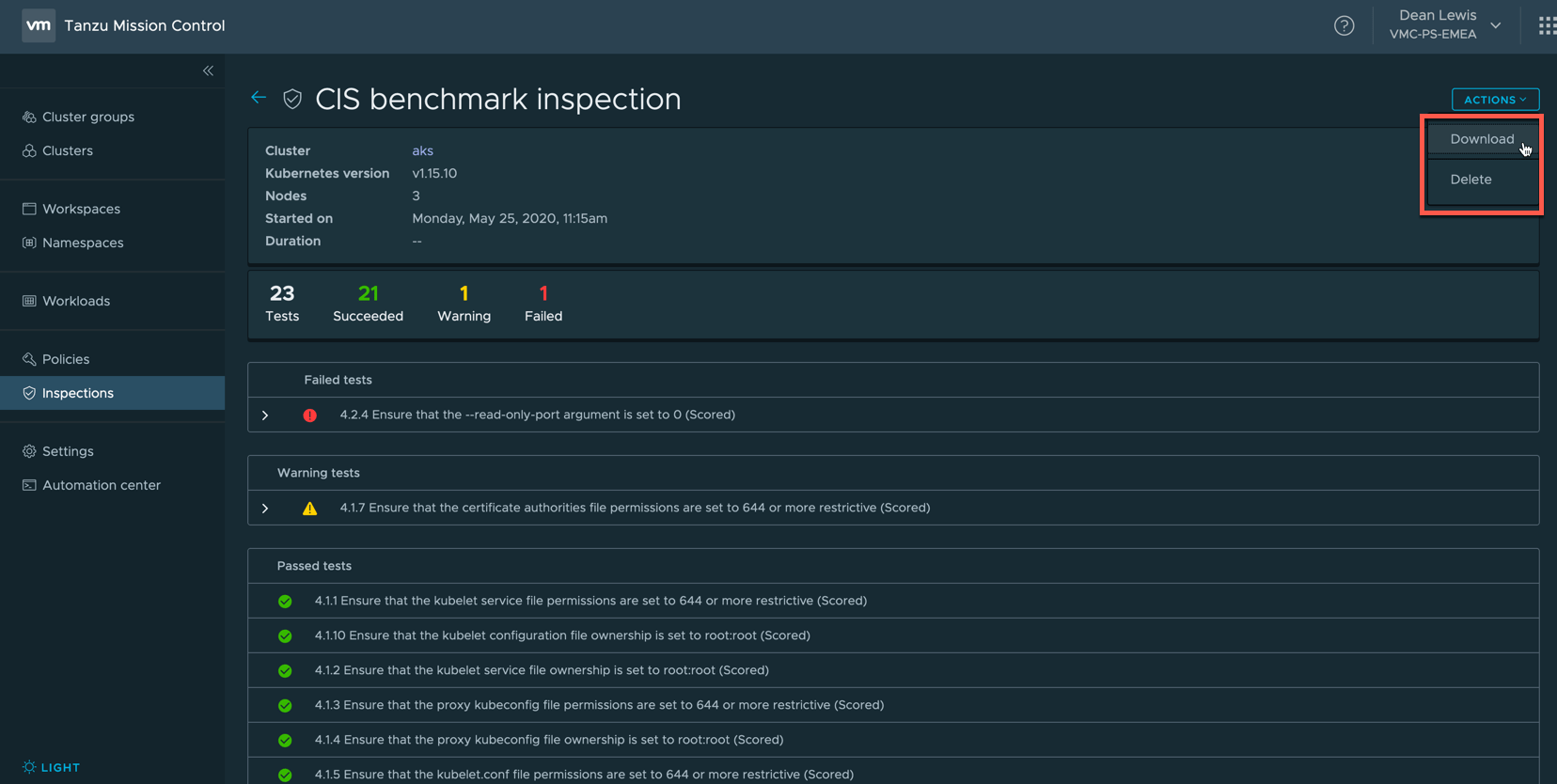
Evaluates your cluster against the CIS Benchmark for Kubernetes published by the Center for Internet Security.
- Lite inspection;
Is a node conformance test that validates whether nodes meet requirements for Kubernetes. For more information, see Validate node setup in the Kubernetes documentation.
Performing Inspections
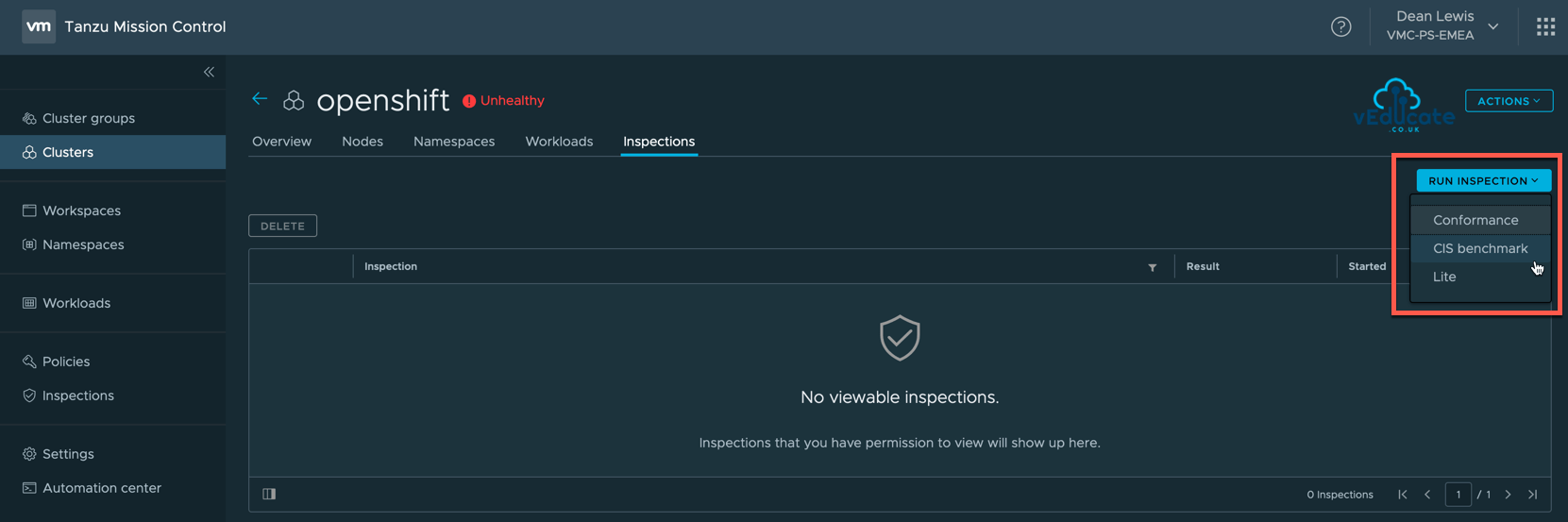
To perform an inspection, there are two ways; from the inspections tab when view a cluster object (as in the above screenshot).
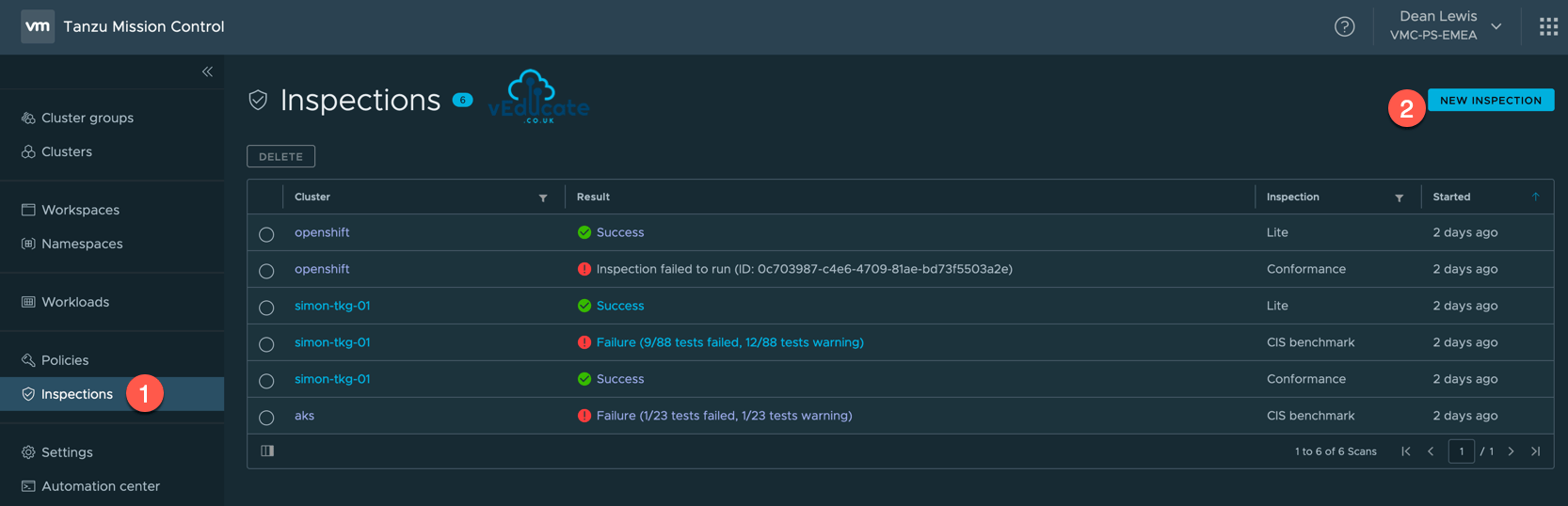
Or you can do this from the Inspections navigation page, as below.
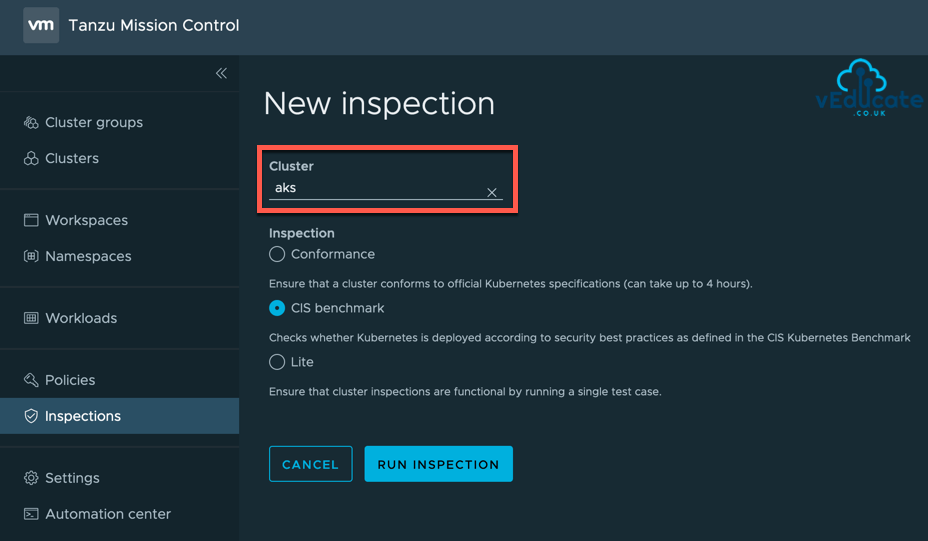
Select your cluster, the inspection type you want to run and click Run Inspection.
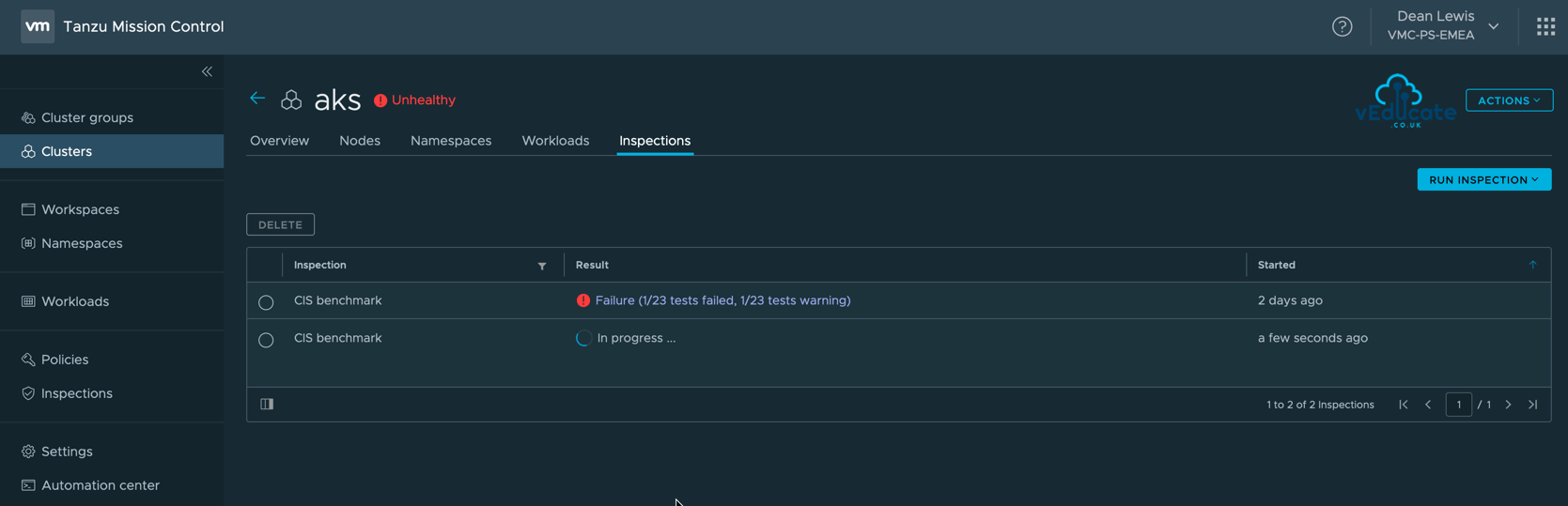
You will then be taken your cluster object inspections page, where you can see your inspection running and the status.
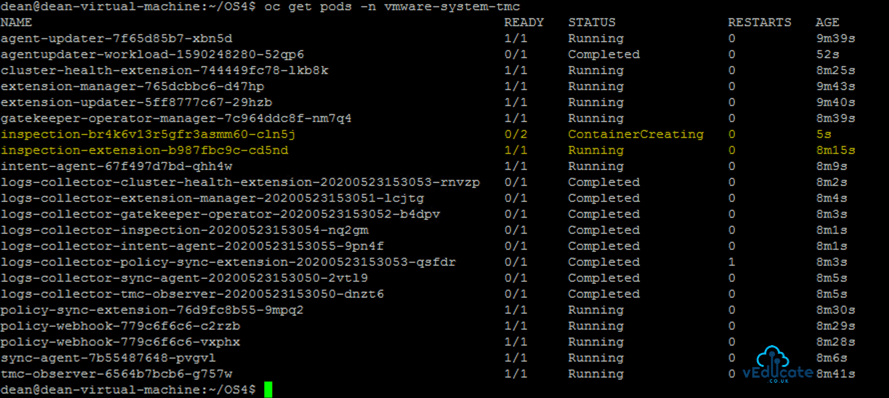
When I log into my cluster, I can see that a new inspection pod is starting. This is the selected inspection service being dynamically started on my environment. Once it has finished, the results will be uploaded to this location, and made available in TMC.
cell-whitesand-aws-usw2-core-47acfezm.s3.amazonaws.com This URL is an AWS S3 bucket in which Tanzu Mission Control stores the results of cluster inspections.
The Inspection-extension pod will already be running as part of the TMC agents that run in your cluster. This service is used to build and execute the Inspection services.
Note: You can only run a single inspection on a cluster at the one time. Trying to run a second scan whilst an existing scan is under way will result in the following
API Error: Failed to create inspection: a scan is already in progress: {SCAN_ID} (failed precondition)
Viewing Inspections
You can view inspections directly from the Inspections tab of the Cluster Object view.
From the Inspections page in the Tanzu Mission Control console, you can view a list of the most recent inspections that have been run against all the clusters in your organization, along with the results of those inspections.
Clicking the report status will show you report itself, which you can also download.
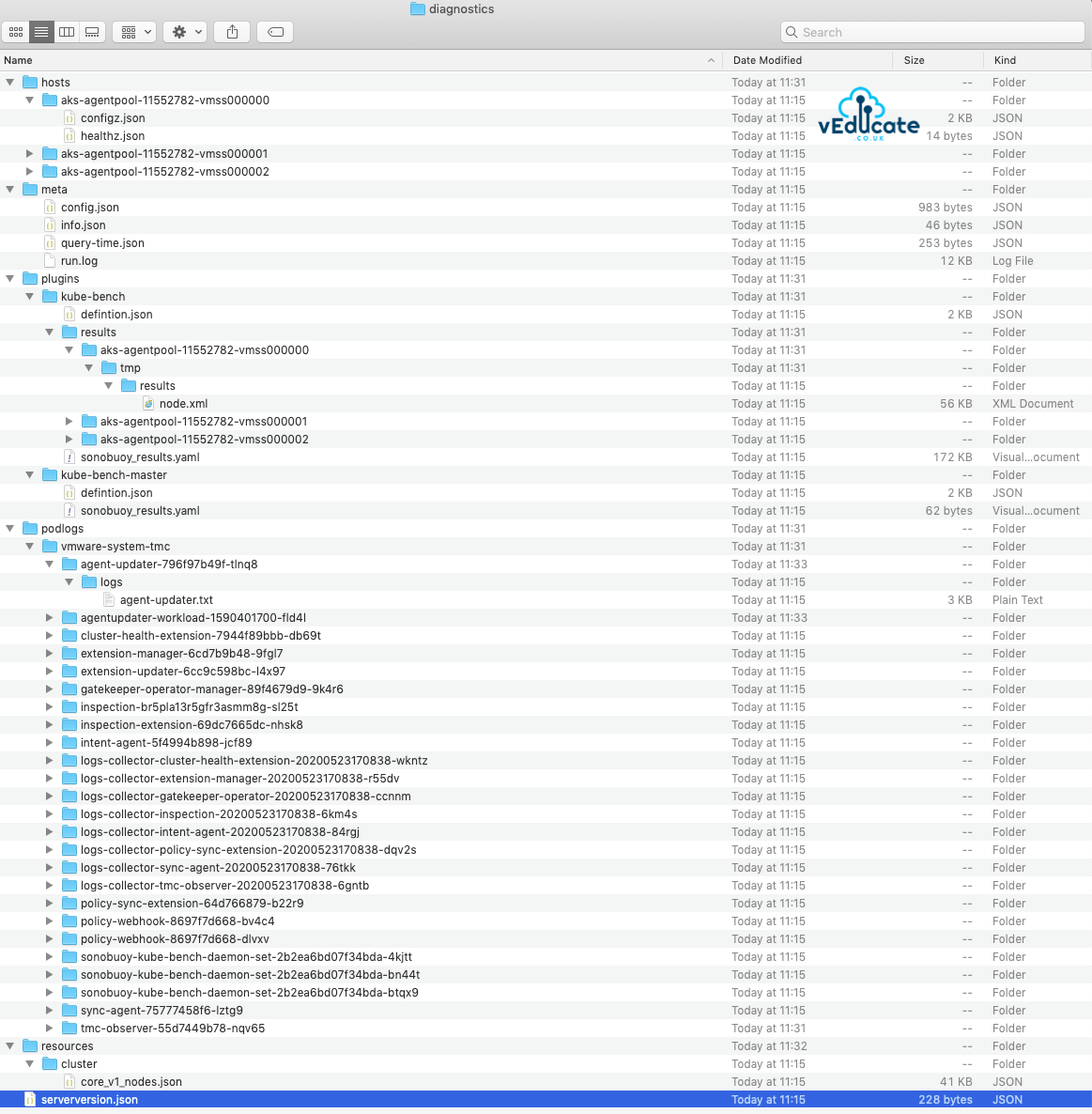
Below is a view of the files downloaded into .tar.gz archive. Which essentially is the output of Sonobuoy, in the above view the TMC services are building these logs into a nicer UI format to consume.
Wrap-up and Resources
In Summary, the ability to run inspections on your clusters can be very a very powerful tool. It is an area I expect VMware will continue to build on in the future.
As a reminder, to take real advantage of TMC I recommend you read the follow posts;
Tanzu Mission Control - Getting Started Tanzu Mission Control - Cluster Inspections - Workspaces and Policies - Data Protection - Deploying TKG clusters to AWS - Upgrading a provisioned cluster - Delete a provisioned cluster - TKG Management support and provisioning new clusters - TMC REST API - Postman Collection - Using custom policies to ensure Kasten protects a deployed application
You can get hands on experience of Tanzu Mission Control yourself over on the VMware Hands-on-Lab website, which is always free!
HOL-2032-01-CNA – VMware Tanzu Mission Control
- In this lab you will be exposed to various aspects of VMware’s Tanzu Mission Control including Kubernetes cluster lifecycle management, health checks, environment at a glance monitoring, access policies, and conformance testing.
And I’ll sign off with links to the official resources.
- Tanzu Mission Control
Regards