In this blog post, we will detail a full technical run through on how to deploy Tanzu Kubernetes Grid (TKG) into Microsoft Azure,
This will be using the new Tanzu CLI (version 1.3) (Previously TKG CLI) released in March 2021, to deploy both a new Management Cluster and Guest Cluster.
Tanzu Kubernetes Grid Cluster Types
TKG has two types of clusters, for the full information of TKG Concepts, please read this post.
- Management Cluster
This is the first architectural components to be deployed for creating a TKG instance. The management cluster is a dedicated cluster for management and operation of your whole TKG instance infrastructure. A management cluster will have Antrea networking enabled by default. This runs cluster API to create the additional clusters for your workloads to run, as well as the shared and in-cluster services for all clusters within the instance to use.
It is not recommended that the management cluster be used as a general-purpose compute environment for your application workloads.
- Tanzu Kubernetes (Guest) Clusters
Once you have deployed your management cluster, you can deploy additional CNCF conformant Kubernetes clusters and manage their full lifecycle. These clusters are designed to run your application workloads, managed via your management cluster. These clusters can run different Kubernetes versions as required. These clusters use Antrea networking by default.
These clusters are referred to as Workload Clusters when working with the Tanzu CLI.
I sometimes use the term “Guest” for these clusters, as a cross-over with the vSphere with Tanzu architecture, which has similar concepts as above however uses the terms “Supervisor Cluster” and “Guest Cluster”.
Pre-Requisites
For this blog post, I’ll be deploying everything from my local Mac OS X machine. You will need the following:
- Docker installed with Kubernetes enabled
- For Windows and macOS Docker clients, you must allocate at least 6 GB of memory in Docker Desktop to accommodate the
kindcontainer. See Settings for Docker Desktop in thekinddocumentation.
- For Windows and macOS Docker clients, you must allocate at least 6 GB of memory in Docker Desktop to accommodate the
- Install the Tanzu CLI and the Kubectl tool > Instructions here.
- If you have used the TKG CLI before, then this is now deprecated.
- You can find a full command line reference for Tanzu CLI and a comparison of the TKG CLI commands in this documentation link.
- Install the Azure CLI.
- Register a Tanzu Kubernetes Grid App on Azure
- The full details in the VMware docs for deploying TKG to Azure can be found here.
Login to the Azure CLI and accept the VM EULA
Before we get started, we need to log into the Azure CLI and accept the EULA for the images used for TKG in Azure. These images are updated with each release of the Tanzu CLI (TKG CLI).
az login
az vm image terms accept --publisher vmware-inc --offer tkg-capi --plan k8s-1dot20dot4-ubuntu-2004 --subscription {subscription_id}
Deploying a Management Cluster using the UI
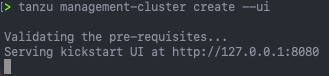
From your terminal, run the following command:
tanzu management-cluster create --ui
 Continue reading Deploying Tanzu Kubernetes Grid Management Cluster to Microsoft Azure
Continue reading Deploying Tanzu Kubernetes Grid Management Cluster to Microsoft Azure