This walk-through will detail the technical configurations for using vRA Code Stream to deploy AWS EKS Clusters, register them as Kubernetes endpoints in vRA Cloud Assembly and Code Stream, and finally register the newly created cluster in Tanzu Mission Control.
This post mirrors my original blog post on using vRA to deploy AWS EKS clusters.
Requirement
Tanzu Mission Control has some fantastic capabilities, including the ability to deploy Tanzu Kubernetes Clusters to various platforms (vSphere, AWS, Azure). However today there is no support to provision native Azure AKS clusters, it can however manage most Kubernetes distributions.
Therefore, when I was asked about where VMware could provide such capabilities, my mind turned to the ability to deploy the clusters using vRA Code Stream and provide additional functions on making these AKS clusters usable.
High Level Steps
- Create a Code Stream Pipeline
- Create an Azure AKS Cluster
- Create AKS cluster as endpoint in both Code Stream and Cloud Assembly
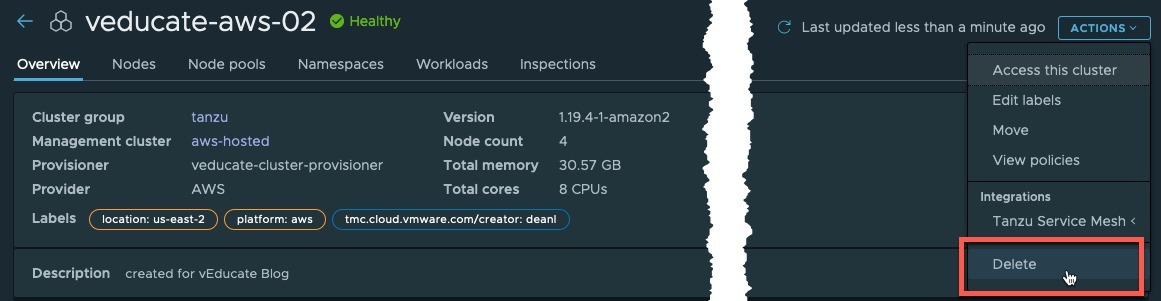
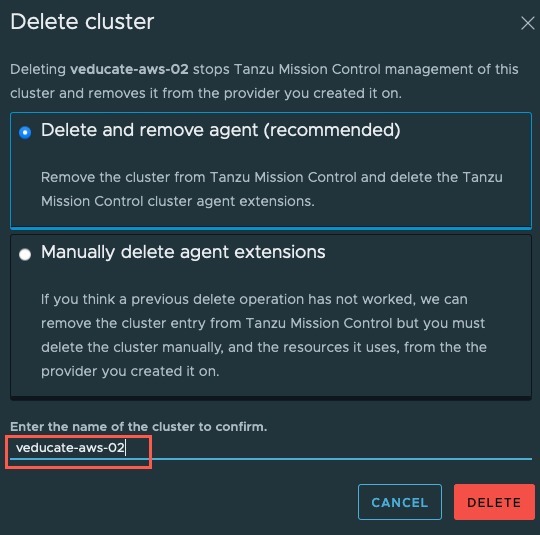
- Register AKS cluster in Tanzu Mission Control
- Export the SSH keys for the AKS cluster to the docker host.
- See this blog post for this bit!
Pre-Requisites
- vRA Cloud access
- The pipeline can be changed easily for use with vRA on-prem
- Azure Account that can provision AKS clusters
- And basic knowledge of deploying AKS cluster
- This is a good beginners guide if you need
- You will need to create a Service Principal that the Azure CLI tool can login with
- A Docker host to be used by Code Stream
- Ability to run the container image: mcr.microsoft.com/azure-cli
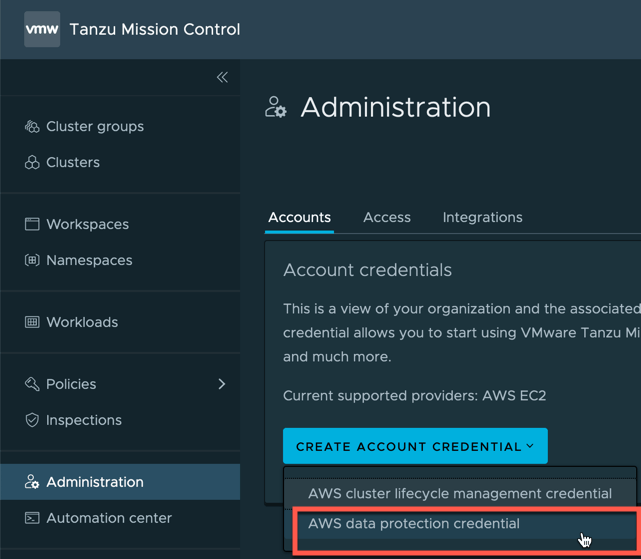
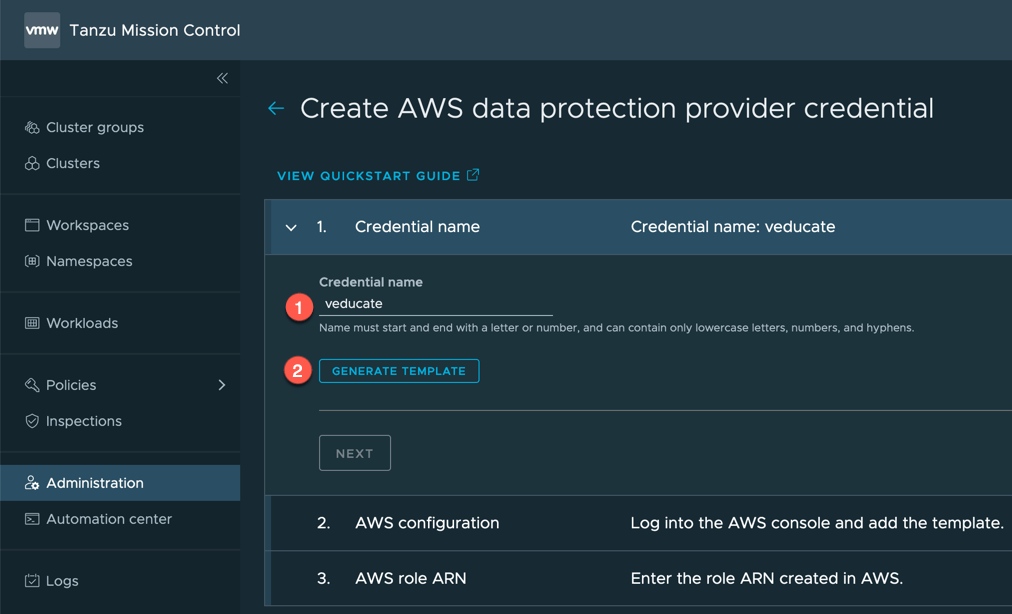
- Tanzu Mission Control account that can register new clusters
- VMware Cloud Console Tokens for vRA Cloud and Tanzu Mission Control API access
- The configuration files for the pipeline can be found in this GitHub repository
Creating a Code Stream Pipeline to deploy a Azure AKS Cluster and register the endpoints with vRA and Tanzu Mission Control
Create the variables to be used
First, we will create several variables in Code Stream, you could change the pipeline tasks to use inputs instead if you wanted. Continue reading Using vRA to deploy Azure AKS Clusters and register with Tanzu Mission Control