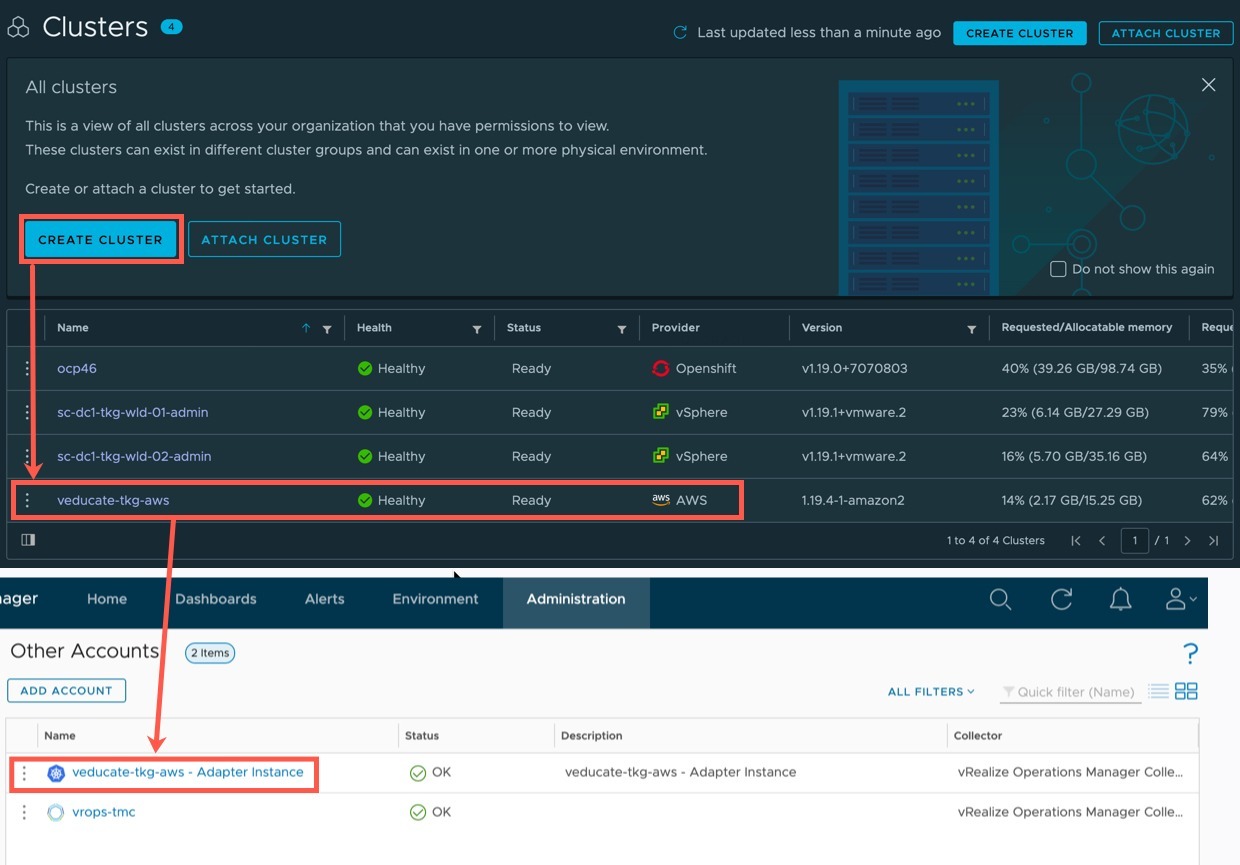
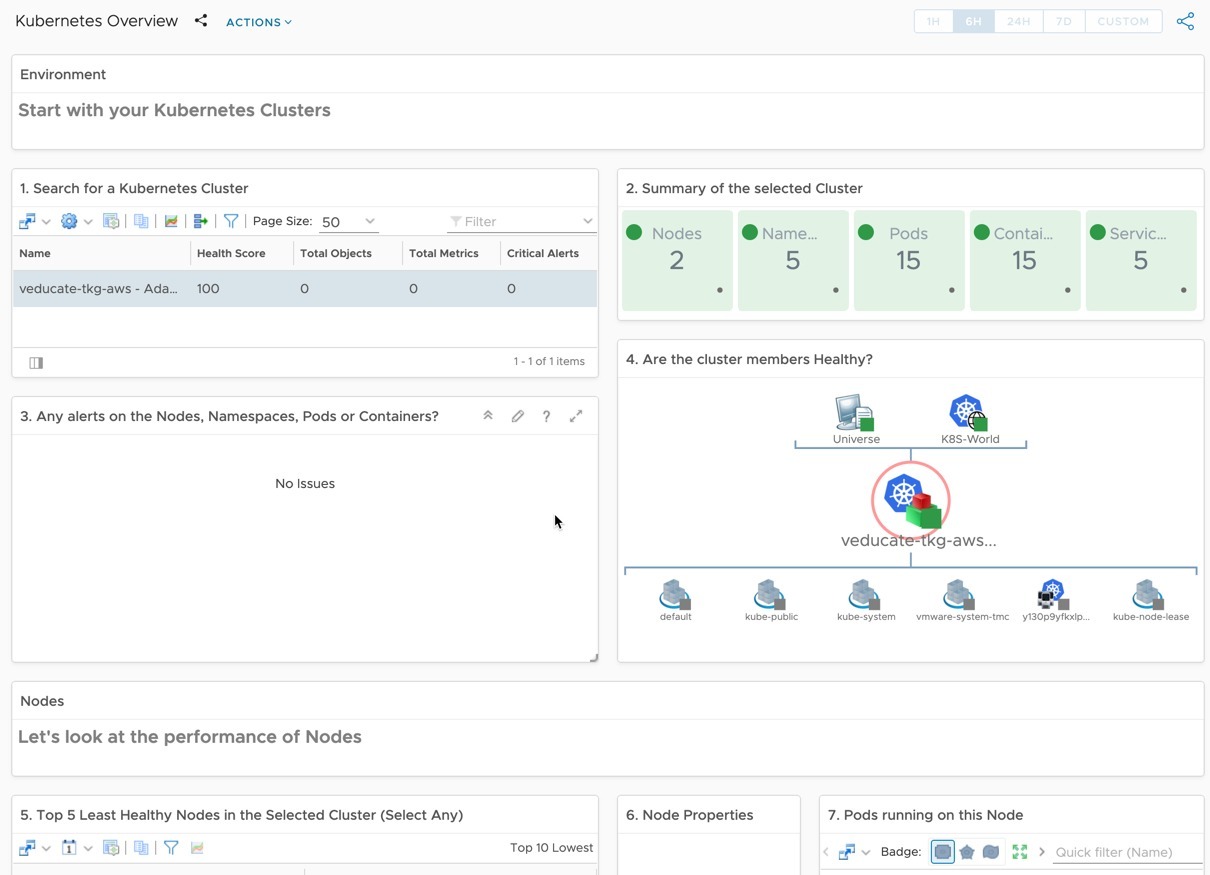
This blog post will cover a technical walk-through on using Tanzu Mission Control to deploy Tanzu Kubernetes clusters to AWS.
The follow up blog posts in this series are:
Tanzu Mission Control - Getting Started Tanzu Mission Control - Cluster Inspections - Workspaces and Policies - Data Protection - Deploying TKG clusters to AWS - Upgrading a provisioned cluster - Delete a provisioned cluster - TKG Management support and provisioning new clusters - TMC REST API - Postman Collection - Using custom policies to ensure Kasten protects a deployed application
Using the AWS Hosted Management Cluster
In this example, we will use the default provided AWS Hosted Management cluster.
Alternatively, you can use the Tanzu CLI to provision a TKG Management cluster into AWS and attach this to Tanzu Mission Control.
Currently it is not supported to have a Management Cluster manage clusters across platforms.
- I.e. Management Cluster in AWS that manages workload clusters in Azure.
To get started:
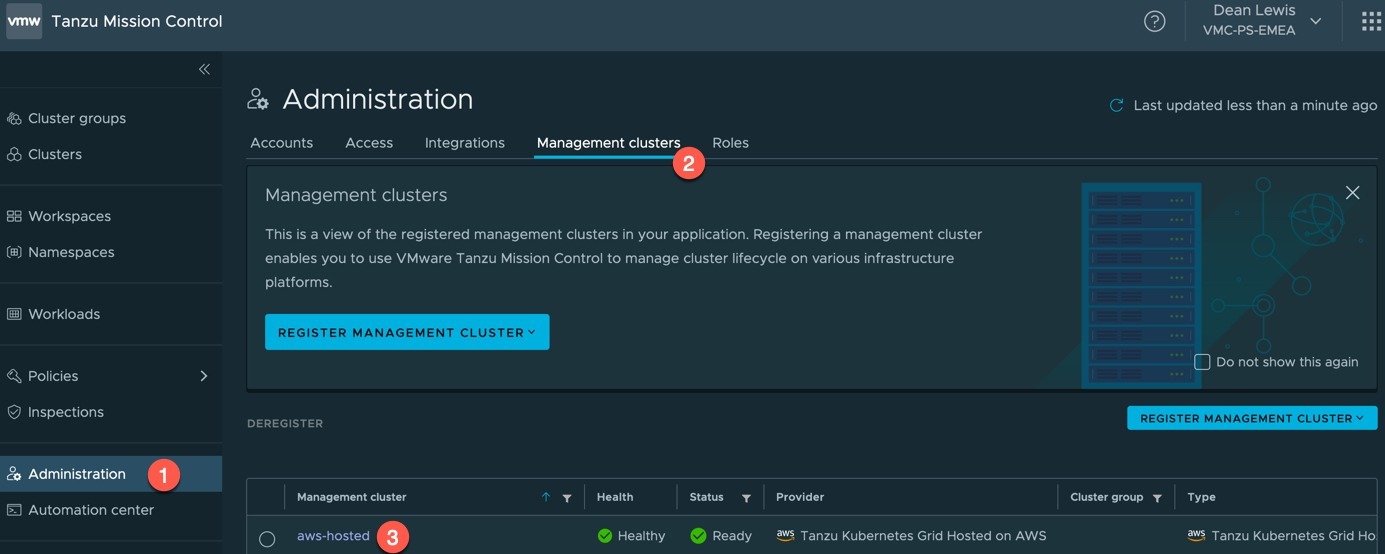
- Go to Administration
- Click the Management Clusters Tab
- Click on the “aws-hosted” cluster object name
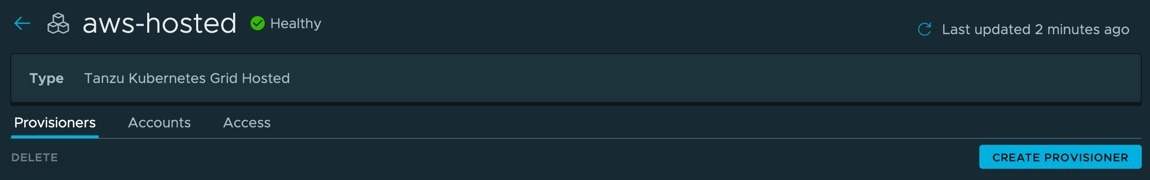
Create a provisioner
The default tab when selecting the “aws-hosted” management cluster object is the provisioner tab.
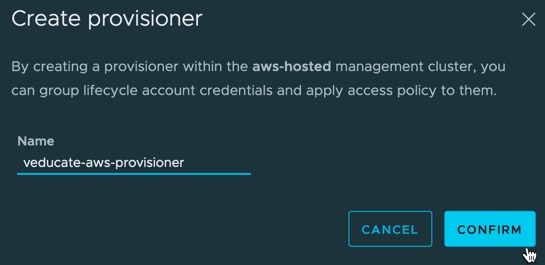
- Click create provisioner
- Provide a name for the provisioner
- Click confirm
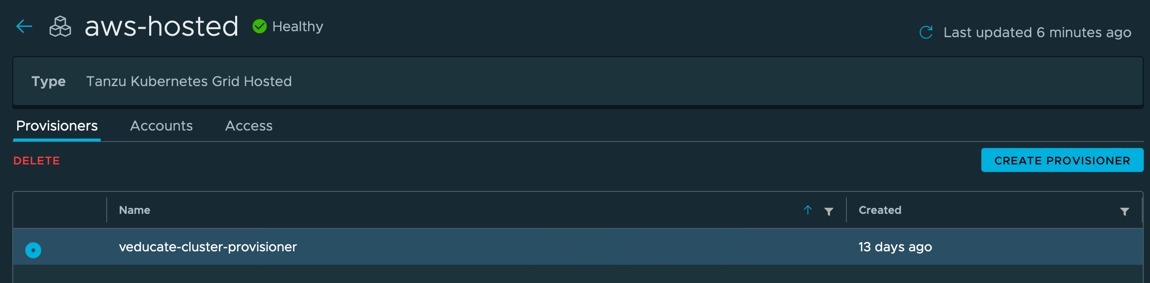
You will be taken back to your provisioner object which is created. Using the radio button to select the object will allow you to delete it. No other action is available.
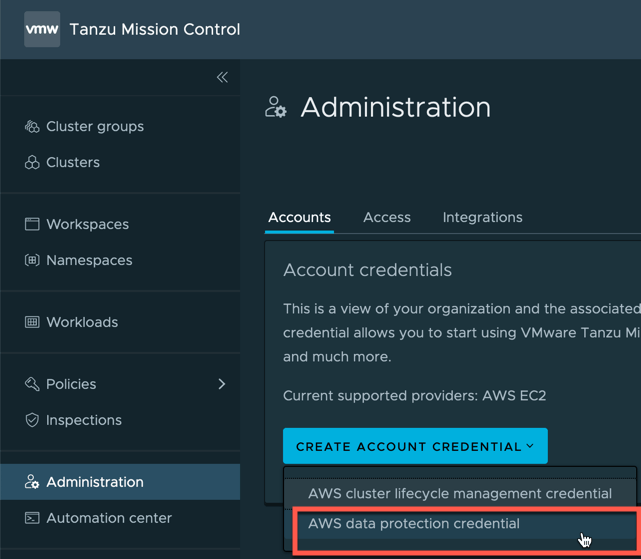
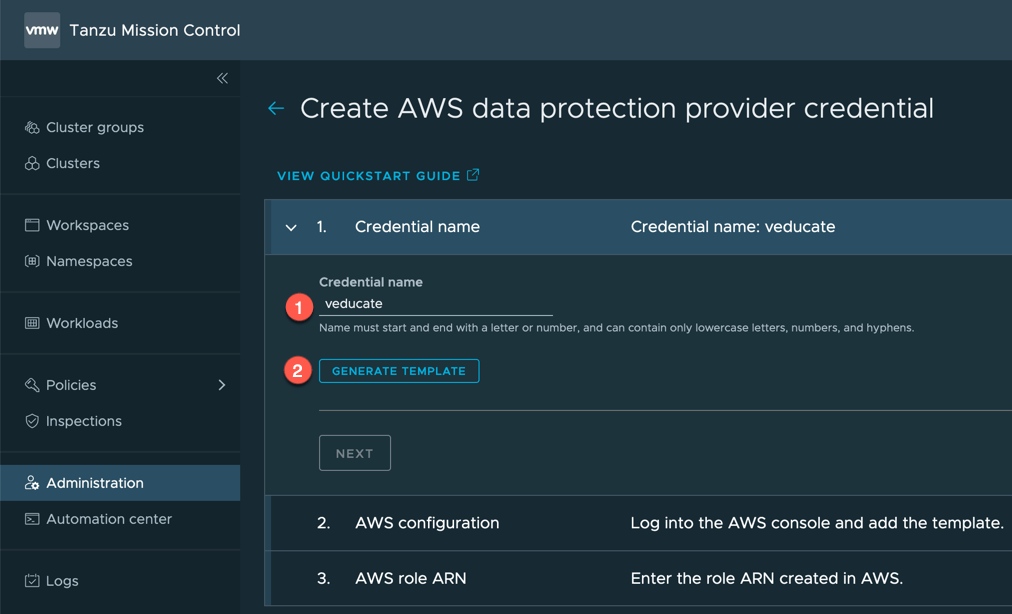
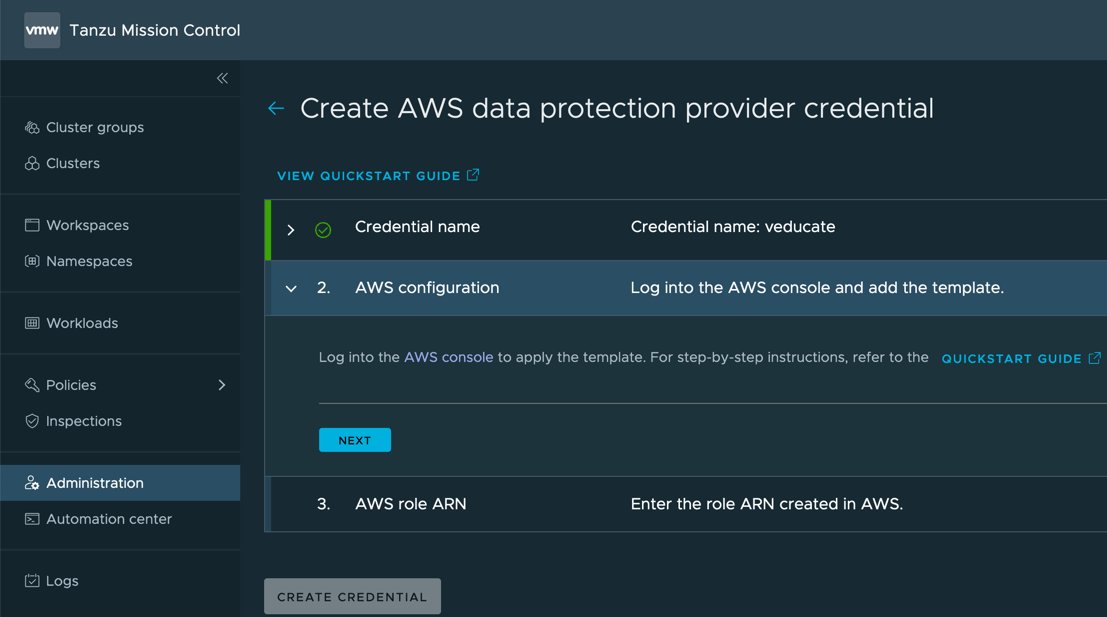
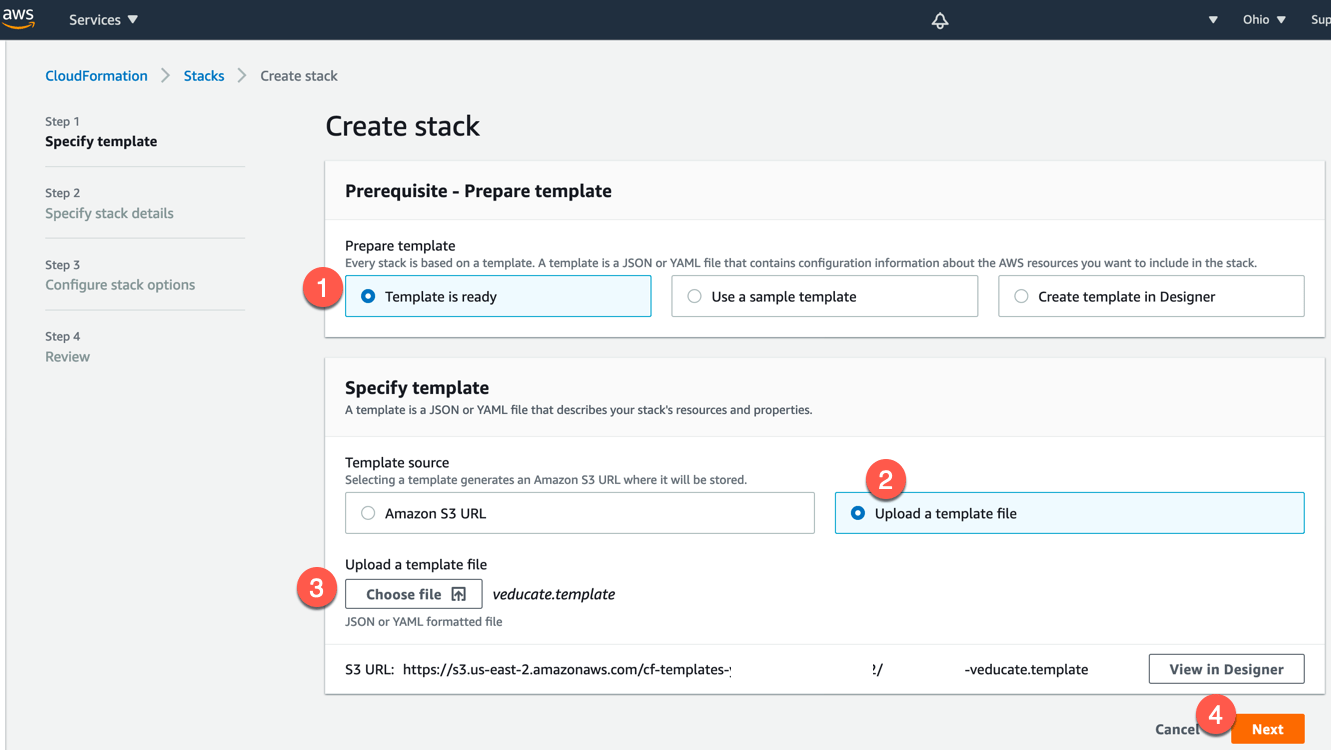
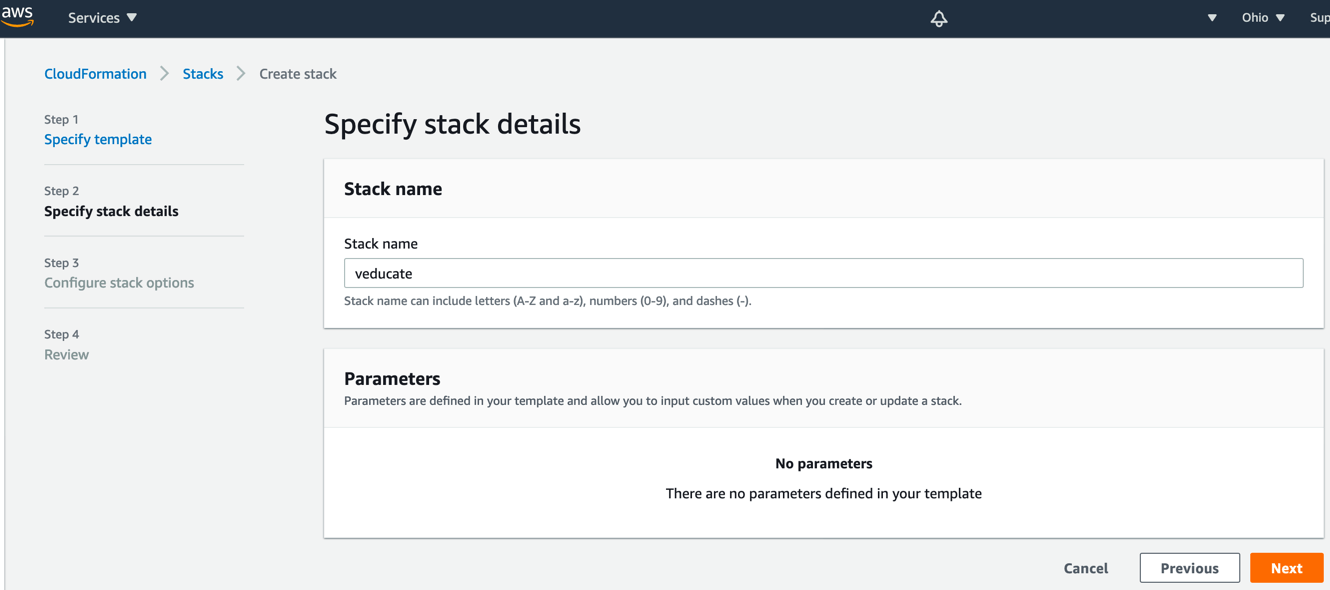
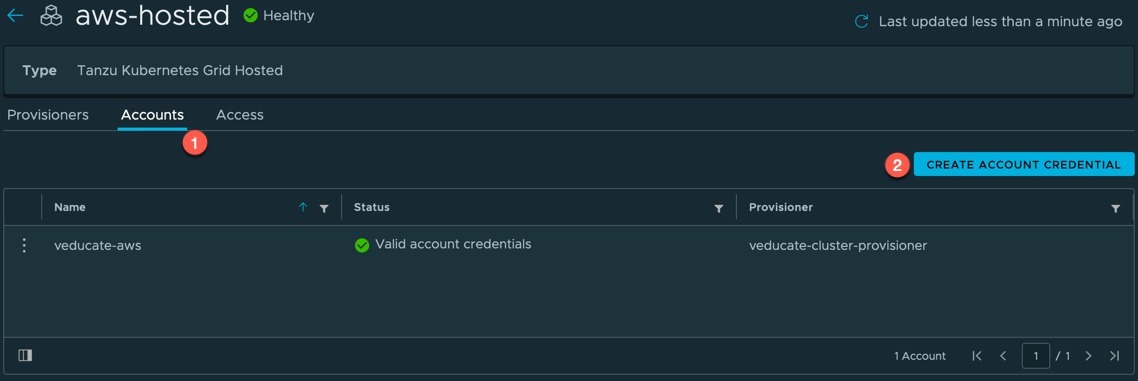
Create the AWS account
- Click on accounts tab
- Click the “Create Account Credential” Button
 Continue reading Tanzu Mission Control – Deploying TKG Clusters to AWS
Continue reading Tanzu Mission Control – Deploying TKG Clusters to AWS